Hello anyone,
I have the following problem:
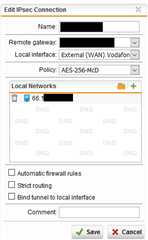
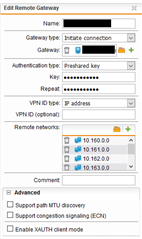
I have a site-to-site IPSec VPN up and running between our SG120 and a customers Cisco ASR Router. However I am not able to get my traffic through the tunnel.
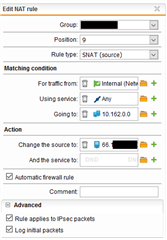
The problem is - as I assume - that I was given an IP address from the customer that I should use as the source IP within the tunnel. This IP is from a public range (66.x.x.x). Now this IP is specified at my side as the local network for my IPSec definition. Otherwise the tunnel will not come up.
When I try to ping any IP on the remote side I don't receive a reply. Also the guy from the "other side" doesn't see any requests from my network through the tunnel. That is no wonder as a traceroute is going out to the internet.
How am I supposed to configure my UTM to send traffic for the destination through the tunnel with the given IP as source address?
Any help is appreciated.
Thanks
Daniel
This thread was automatically locked due to age.