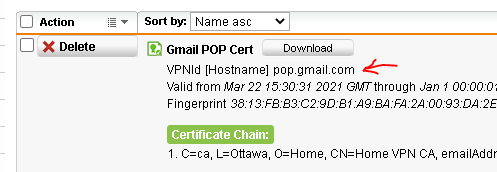
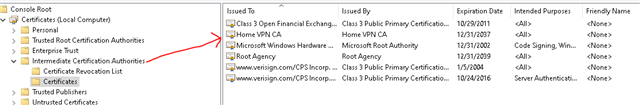
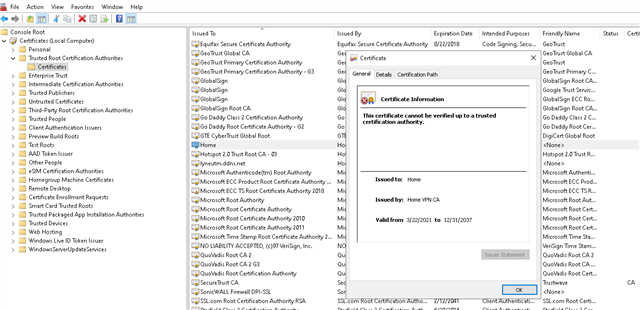
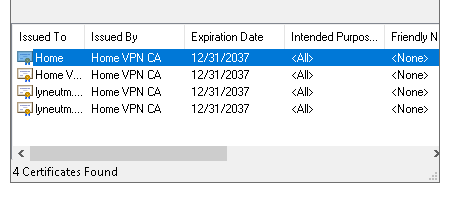
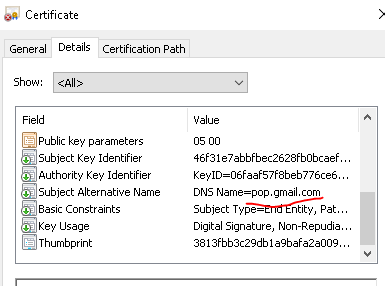
I have Sophos UTM 9.7 scanning my emails using Oultook client but whenever I start outlook it complains about the self signed certificate. If I view the certificate it does allow me to install it and I said yes but that doesn't fix the problem
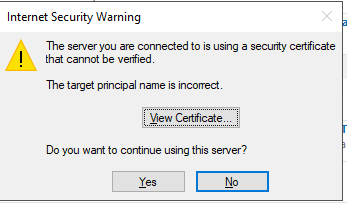
In Sophos I selected the local cert as I don't have one specifically for Outlook (or for anything, actually). If I don't select to scan TLS traffic, nothing gets scanned as all my email accounts use TLS.
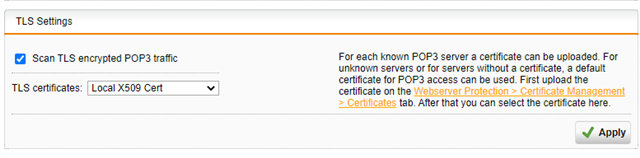
What do I need to do to make it is so Outlook doesn't ask me about cert every time I start it?
Any info would be appreciated
This thread was automatically locked due to age.