Hi,
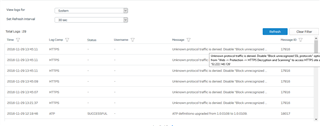
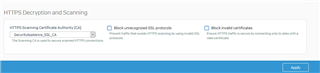
Currently my device XG-135 is running on V16.01.2, and it is weird to see that it is blocking unknown protocol traffic. Although "Block unrecognized SSL protocol " option is disabled under Web--> Protection. Below screenshots for reference.
Please suggest how to resolve this issue. There was no such issue until V15 & V16, all began after 16.01.2 .
This thread was automatically locked due to age.