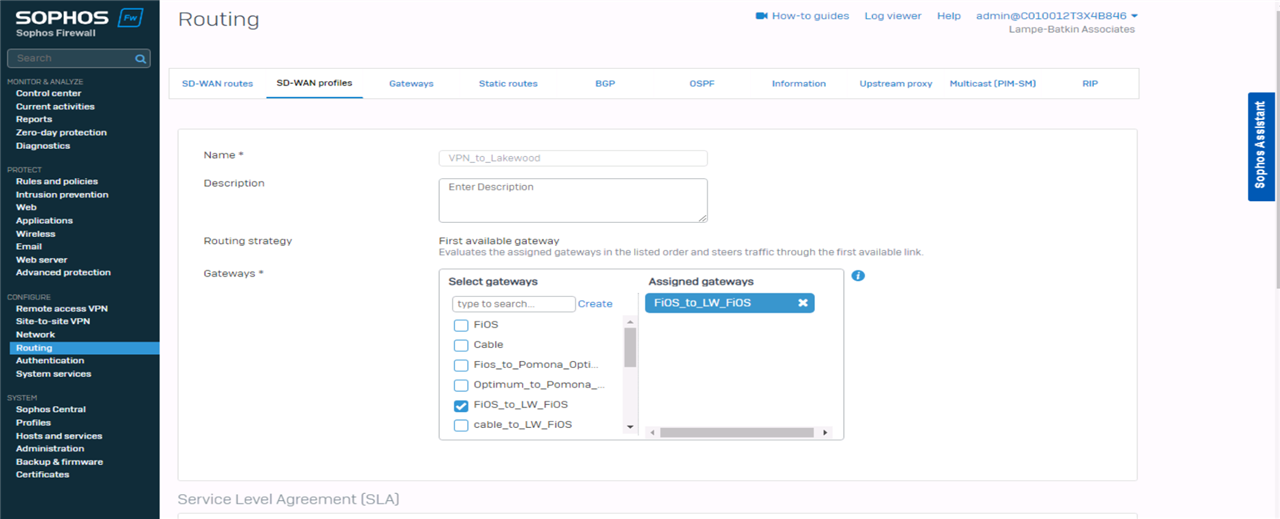
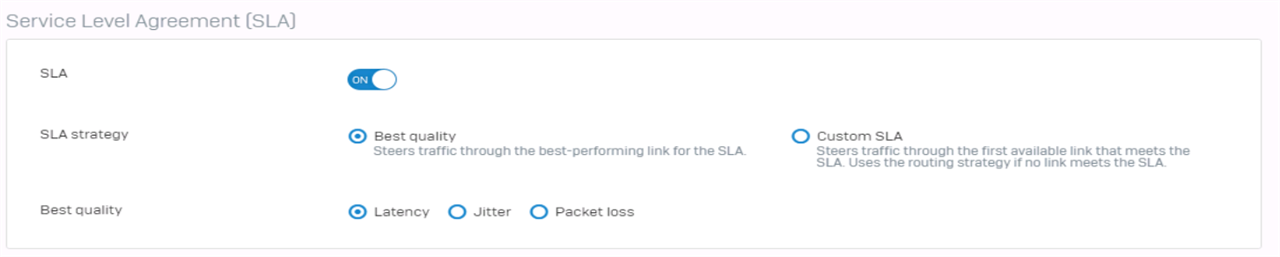
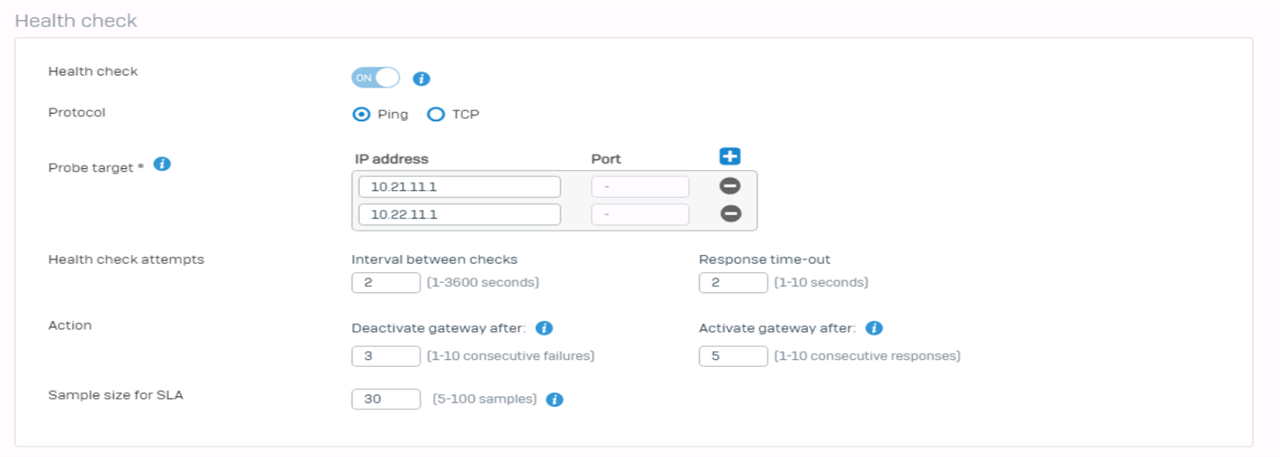
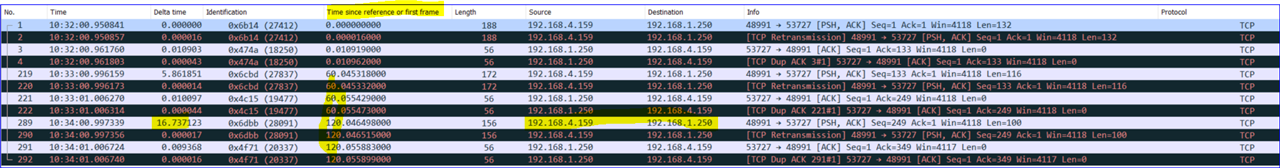
I have XG V19 Firewalls and created a SD-WAN policy to handle traffic for Site 2 Site Route based IPSec VPN with xfrm interfaces.
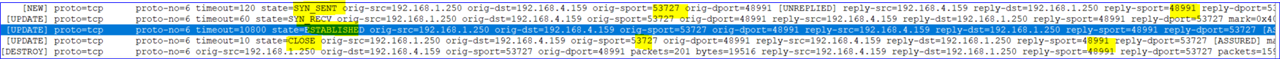
it works great, just some strange issue, many application that are used over that VPN timeout and crash after around 15 - 20 minutes,
so if a user has open an RDP session it will suddenly crash
This thread was automatically locked due to age.