Hello,
We have a clients-server based application, where the server is in a different vlan as the clients.
The communication between both vlans is routed via SophosXG VLAN Interfaces. (XG430 / 18.5MR1)
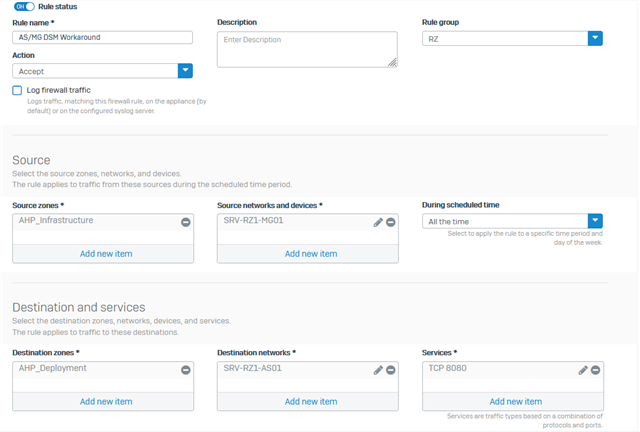
The GUI firewall rules are configured to allow everything for both vlan-networks in each direction.
However, this client-server based application doesn't work with this setup.
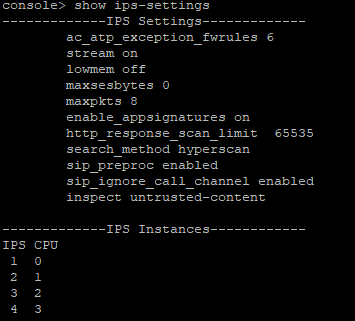
Only way to get the application working as expected is to set advanced-firewall bypass via CLI
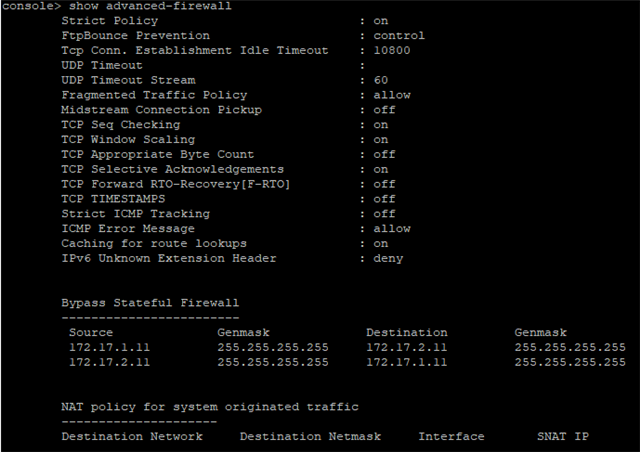
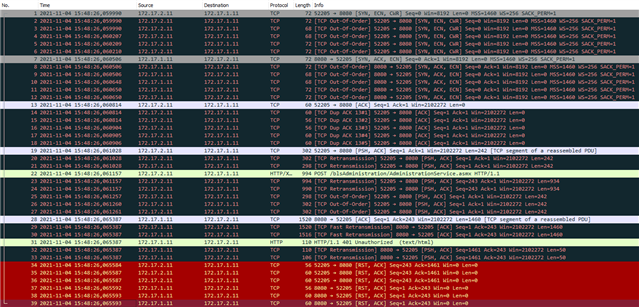
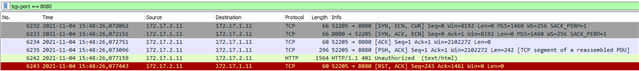
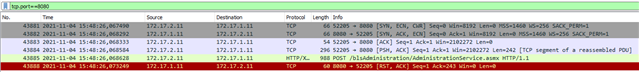
I assume that the application is not working 100% RFC conform and for example the XG tcp-seq-checking drops the packege.

My problem is, I cant see any dropped packeg in any log on XG firewall.
I need to know exactly why the firewall is dropping that traffic in order to contact the application vendors if something is not RFC compliant at application side.
Can you please tell me how to log such kind of drops from the advanced-firewall checks.
Thank you for help!
This thread was automatically locked due to age.