Dear all,
someone can help me to understand what i missed?
The whole company is working fine, but, i was working on two new laptop and only this two didn´t reach some internet websites (youtube, spotify, soundcloud and similar),
At the beginning, as also you can notice from the tipology of the websites, sound like a web filter problem, but also with a specific rule on the firewall with the webfilter "allow all" i have the same problem.
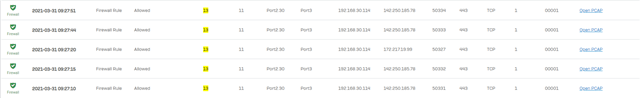
on the logs i have, randomly, this:
but on the config the Spoof control is deactivated.
as config i have two XG135 in HA config with the (SFOS 18.0.4 MR-4)
Some one have some tip?
This thread was automatically locked due to age.