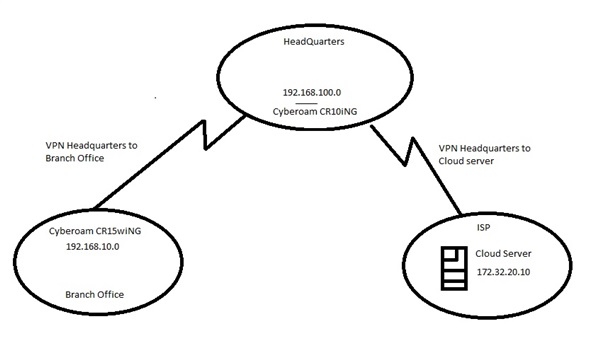
Hello guys
I have a Cyberoam CR10 at the Headquarters and aCyberoam CR15 in another branch office. The Headquarters Cyberoam is connected to another VPN that we communicate with a clouds server 172.32.20.10. Sorry about the image.
Can you please tell me if its possible the Branch office users to communicate with the Cloud Server. Can I create a static route at the Branch office Cyberoam saying that if I want to see 172.32.20.10 go through the external interface of Headquarters Cyberoam? Anyone has an idea?
Thank you
This thread was automatically locked due to age.