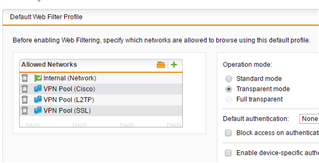
So, avoiding split tunneling (although, i wouldn't even know how to configure that), how would I allow all traffic to be filtered through the VPN? At the moment, I have setup SSL on my SophosUTM 9.4 box. I can connect and fetch anything I need from within the network, but since split tunneling is not functioning (and I really don't want it to be functioning) all access is restricted to the inside network.
Now, I'd would like to access the internet while connected to my VPN but through an additional interface (third one) to the SophosUTM box. Is there any way to do this, route all traffic through that third interface when I'm out and about.
Can someone please instruct me on how to do this?
Appreciation in advance
This thread was automatically locked due to age.