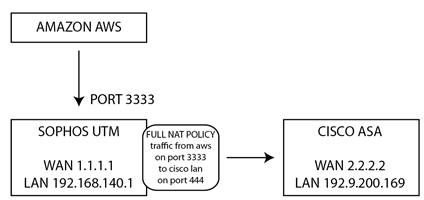
Our connection seems to be completing phase 1, but is failing on a matched/mismatched Pair ID. The thing is that the pair id actually matches, but the log says that it doesn't, but shows the same two words there.
I don't have access to the actual cisco box, it is with an external vendor. Here are the respective logs.
CISCO LOG
Mar 31 2017 08:21:08: %ASA-5-713201: Group = 1.1.1.1, IP = 1.1.1.1, Duplicate Phase 1 packet detected. Retransmitting last packet.
Mar 31 2017 08:21:08: %ASA-6-713905: Group =1.1.1.1, IP =1.1.1.1, P1 Retransmit msg dispatched to MM FSM
Mar 31 2017 08:21:08: %ASA-7-713906: Received unexpected event EV_RESEND_MSG in state MM_REKEY_DONE_H2
Mar 31 2017 08:20:58: %ASA-5-713068: Group =1.1.1.1, IP =1.1.1.1, Received non-routine Notify message: Invalid ID info (18)
SOPHOS LOG
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n]
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: ignoring Vendor ID payload [FRAGMENTATION c0000000]
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: enabling possible NAT-traversal with method RFC 3947
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: ignoring Vendor ID payload [Cisco-Unity]
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: received Vendor ID payload [XAUTH]
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: ignoring Vendor ID payload [26af64ae1ce2e355e599171584afb948]
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: ignoring Vendor ID payload [Cisco VPN 3000 Series]
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike-02/03: peer is NATed
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: received Vendor ID payload [Dead Peer Detection]
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: Peer ID is ID_KEY_ID: 'abc'
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: we require peer to have ID 'abc', but peer declares 'abc'
2017:03:31-10:06:52 50 pluto[3800]: "S_KWIK-2" #1: sending encrypted notification INVALID_ID_INFORMATION to 2.2.2.2:4500
This thread was automatically locked due to age.