So i have no other choice but to post here ans hope for the best.
I have Sophos UTM9 on an ESX server at my house and at my buddies business.
Both locations are behind a NAT router, my home setup has a ZyWall SUG20 as the main gateway/router.
I (so far atleast) have setup SNAT and Firewall rules to the UTM at home and have the UTM at home being the responder.
The UTM at the business is behind those crappy AT&T DSL modems that are all in one but i do have the ports to the UTM WAN NAT IP open.
So far i have been able to get the two UTM's to talk to each other but the VPN connection is throwing errors i don't understand.
Home Setup:
Modem (Public IP 71.65.xxx.xxx -> ZyWall USG20 (LAN 192.168.4.1) to esx/Sophos VM (WAN 192.168.4.2 LAN 192.168.2.1)
Business Setup:
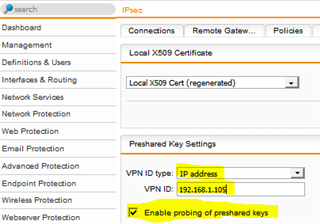
DSL Modem/Router/Gateway (Public IP 66.95.xxx.xxx -> ESX/Sophos VM (WAN 192.168.1.105 LAN 192.168.1.253)
I have the initial connection from Business Sophos UTM to gateway 71.65.xxx.xxx
Gateway: 71.64.xxx.xxx
Pre-shared key auth
no VPN ID
Remote Networks 192.168.2.1/24
Local Interface (NAT WAN IP - 192.168.1.105)
Local Networks 192.168.1.0/24
Policy AES-256
This is the Responder setup at my house behind the ZyWall
pre-shared key auth
Any VPN ID Type
Any VPN ID
Remote network: 192.168.1.0/24
Gateway: Any (responder setup)
Local interface: NAT WAN IP 192.168.4.2
Local Networks: Internal Network 192.168.2.0/24
Policy: AES-256
I allowed the firewall on both UTM's to allow all traffic everywhere and i also added a Multipath Rule to test with to.
I'm not sure what other info is needed as this is my first time setting up a site to site outside of a Cisco lab and i've never done anything with VPN behind NAT so i'm kind confused.
This is my Responder Gateway log from home:
2017:01:05-13:46:30 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #55: NAT-Traversal: Result using RFC 3947: both are NATed
2017:01:05-13:46:30 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #55: Peer ID is ID_IPV4_ADDR: '192.168.1.105'
2017:01:05-13:46:30 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #55: Dead Peer Detection (RFC 3706) enabled
2017:01:05-13:46:30 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #55: sent MR3, ISAKMP SA established
2017:01:05-13:46:30 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #55: ignoring informational payload, type INVALID_ID_INFORMATION
2017:01:05-13:46:40 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #53: DPD: Phase1 state #53 has been superseded by #55 - timeout ignored
2017:01:05-13:46:41 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #55: retransmitting in response to duplicate packet; already STATE_MAIN_R3
2017:01:05-13:46:41 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #55: ignoring informational payload, type INVALID_ID_INFORMATION
2017:01:05-13:47:01 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #55: retransmitting in response to duplicate packet; already STATE_MAIN_R3
2017:01:05-13:47:01 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #55: ignoring informational payload, type INVALID_ID_INFORMATION
2017:01:05-13:47:37 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #54: DPD: Phase1 state #54 has been superseded by #55 - timeout ignored
2017:01:05-13:47:41 sophos pluto[9652]: packet from 99.65.xxx.xxx:4500: received Vendor ID payload [strongSwan]
2017:01:05-13:47:41 sophos pluto[9652]: packet from 99.65.xxx.xxx:4500: ignoring Vendor ID payload [Cisco-Unity]
2017:01:05-13:47:41 sophos pluto[9652]: packet from 99.65.xxx.xxx:4500: received Vendor ID payload [XAUTH]
2017:01:05-13:47:41 sophos pluto[9652]: packet from 99.65.xxx.xxx:4500: received Vendor ID payload [Dead Peer Detection]
2017:01:05-13:47:41 sophos pluto[9652]: packet from 99.65.xxx.xxx:4500: received Vendor ID payload [RFC 3947]
2017:01:05-13:47:41 sophos pluto[9652]: packet from 99.65.xxx.xxx:4500: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03]
2017:01:05-13:47:41 sophos pluto[9652]: packet from 99.65.xxx.xxx:4500: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02]
2017:01:05-13:47:41 sophos pluto[9652]: packet from 99.65.xxx.xxx:4500: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n]
2017:01:05-13:47:41 sophos pluto[9652]: packet from 99.65.xxx.xxx:4500: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
2017:01:05-13:47:41 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #56: responding to Main Mode from unknown peer 99.65.xx.xx:4500
2017:01:05-13:47:41 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #56: NAT-Traversal: Result using RFC 3947: both are NATed
2017:01:05-13:47:41 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #56: Peer ID is ID_IPV4_ADDR: '192.168.1.105'
2017:01:05-13:47:41 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #56: Dead Peer Detection (RFC 3706) enabled
2017:01:05-13:47:41 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #56: sent MR3, ISAKMP SA established
2017:01:05-13:47:41 sophos pluto[9652]: "S_Respond"[2] 99.65.xxx.xxx:4500 #56: ignoring informational payload, type INVALID_ID_INFORMATION
This is the log from initiated connection at the business:
2017:01:05-13:50:02 sophosutm pluto[13827]: "S_Connect" #58: received Vendor ID payload [strongSwan]
2017:01:05-13:50:02 sophosutm pluto[13827]: "S_Connect" #58: ignoring Vendor ID payload [Cisco-Unity]
2017:01:05-13:50:02 sophosutm pluto[13827]: "S_Connect" #58: received Vendor ID payload [XAUTH]
2017:01:05-13:50:02 sophosutm pluto[13827]: "S_Connect" #58: received Vendor ID payload [Dead Peer Detection]
2017:01:05-13:50:02 sophosutm pluto[13827]: "S_Connect" #58: received Vendor ID payload [RFC 3947]
2017:01:05-13:50:02 sophosutm pluto[13827]: "S_Connect" #58: enabling possible NAT-traversal with method 3
2017:01:05-13:50:03 sophosutm pluto[13827]: "S_Connect" #58: NAT-Traversal: Result using RFC 3947: both are NATed
2017:01:05-13:50:03 sophosutm pluto[13827]: packet from 71.64.xx.xx:4500: Informational Exchange is for an unknown (expired?) SA
2017:01:05-13:50:03 sophosutm pluto[13827]: "S_Connect" #58: Peer ID is ID_IPV4_ADDR: '192.168.4.2'
2017:01:05-13:50:03 sophosutm pluto[13827]: "S_Connect" #58: we require peer to have ID '71.64xxx.xxx', but peer declares '192.168.4.2'
2017:01:05-13:50:03 sophosutm pluto[13827]: "S_Connect" #58: sending encrypted notification INVALID_ID_INFORMATION to 71.64.xx.xx:4500
2017:01:05-13:50:13 sophosutm pluto[13827]: "S_Connect" #58: Peer ID is ID_IPV4_ADDR: '192.168.4.2'
2017:01:05-13:50:13 sophosutm pluto[13827]: "S_Connect" #58: we require peer to have ID '71.64.xx.xx', but peer declares '192.168.4.2'
2017:01:05-13:50:13 sophosutm pluto[13827]: "S_Connect" #58: sending encrypted notification INVALID_ID_INFORMATION to 71.64.xx.xx:4500
2017:01:05-13:50:28 sophosutm pluto[13827]: "S_Connect" #58: DPD: Received R_U_THERE for unestablished ISAKMP SA
2017:01:05-13:50:33 sophosutm pluto[13827]: packet from 71.64.xx.xx:4500: Informational Exchange is for an unknown (expired?) SA
2017:01:05-13:50:33 sophosutm pluto[13827]: "S_Connect" #58: Peer ID is ID_IPV4_ADDR: '192.168.4.2'
2017:01:05-13:50:33 sophosutm pluto[13827]: "S_Connect" #58: we require peer to have ID '71.64.xx.xx', but peer declares '192.168.4.2'
2017:01:05-13:50:33 sophosutm pluto[13827]: "S_Connect" #58: sending encrypted notification INVALID_ID_INFORMATION to 71.64.xx.xx:4500
2017:01:05-13:50:58 sophosutm pluto[13827]: "S_Connect" #58: DPD: Received R_U_THERE for unestablished ISAKMP SA
2017:01:05-13:51:03 sophosutm pluto[13827]: packet from 71.64.xx.xx:4500: Informational Exchange is for an unknown (expired?) SA
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #58: max number of retransmissions (2) reached STATE_MAIN_I3. Possible authentication failure: no acceptable response to our first encrypted message
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #58: starting keying attempt 50 of an unlimited number
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #59: initiating Main Mode to replace #58
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #59: received Vendor ID payload [strongSwan]
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #59: ignoring Vendor ID payload [Cisco-Unity]
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #59: received Vendor ID payload [XAUTH]
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #59: received Vendor ID payload [Dead Peer Detection]
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #59: received Vendor ID payload [RFC 3947]
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #59: enabling possible NAT-traversal with method 3
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #59: NAT-Traversal: Result using RFC 3947: both are NATed
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #59: Peer ID is ID_IPV4_ADDR: '192.168.4.2'
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #59: we require peer to have ID '71.64.xxx.xx', but peer declares '192.168.4.2'
2017:01:05-13:51:13 sophosutm pluto[13827]: "S_Connect" #59: sending encrypted notification INVALID_ID_INFORMATION to 71.64.xx.xx:4500
This thread was automatically locked due to age.