I used to run OpenSwan EC2 instances to connect two regions. I'm using centralized monitoring for instances with Splunk so I have installed Splunk forwarders on all instances that send their logs to a Splunk Indexer in Ireland. It worked for the most part but the tunnels would drop every month for some reason which would prevent logs from getting sent so I decided to move to Sophos's AWS VPC site-to-site VPN since I can eliminate the two OpenSwan instances. I had no problem sending Splunk traffic with this configuration.
I have two regions that I have connected using Site-to-site VPN --> Amazon VPC configuration in my Sophos UTM 9 appliance.
My UTM 9 Firmware version: 9.405-5
Ireland VPC CIDR = 172.20.0.0/16
Frankfurt VPC CIDR - 10.20.0.0/16
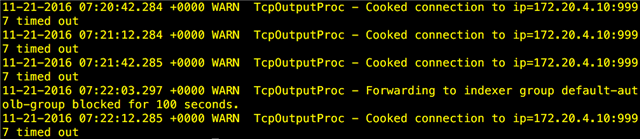
I have a Splunk instance in Ireland - 172.20.4.10 - that is listening on TCP 9997 and all instances have Splunk forwarder agents that send to 172.20.4.10:9997. However, the connection is timing out and I cannot figure out why:
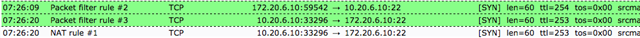
Sophos UTM 9 is showing that the packets are going through:
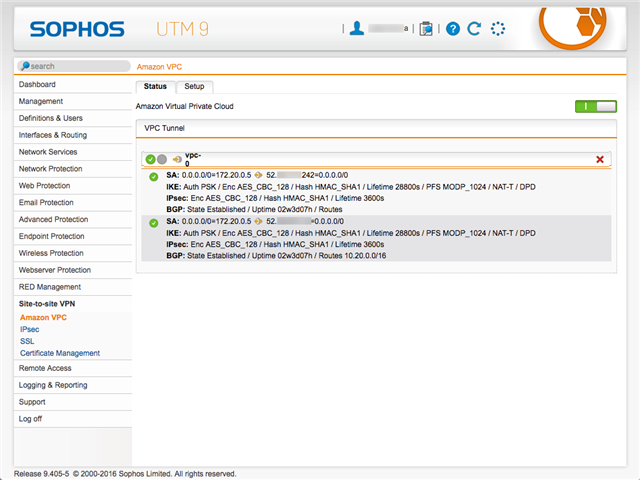
I have successfully configured a site-to-site VPN from a UTM 9 Appliance in Ireland to an AWS Virtual Private Gateway in Frankfurt:
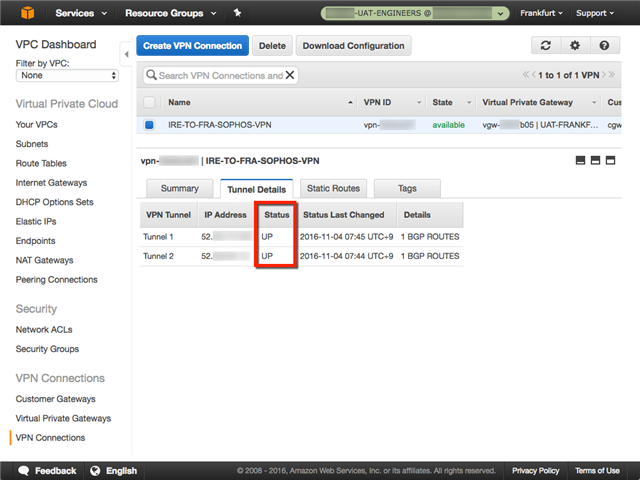
The Frankfurt Tunnel Details show that both tunnels are up:
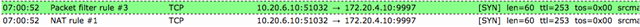
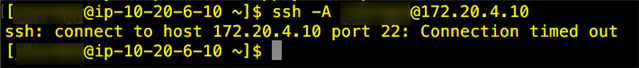
I can SSH between two instances in each region 172.20.6.10 <--> 10.20.6.10:
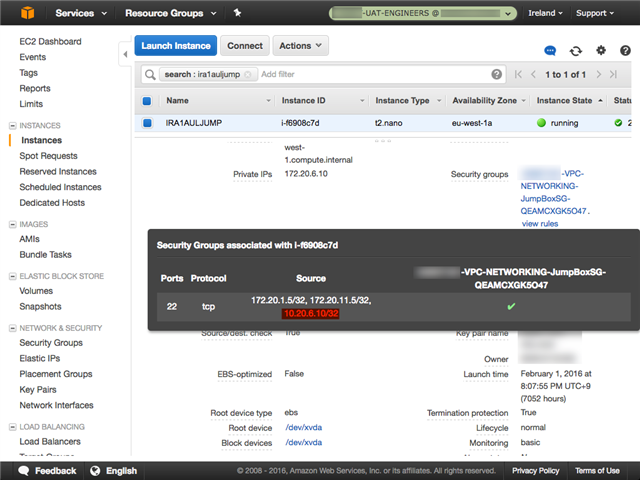
Security group on Ireland instance:
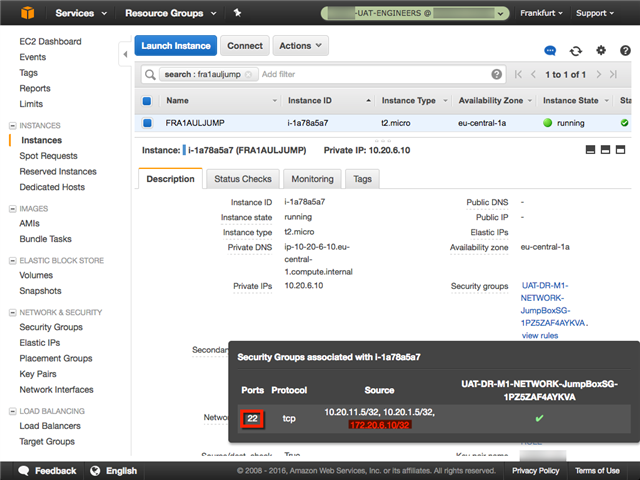
Security group on Frankfurt instance:
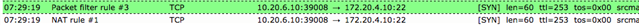
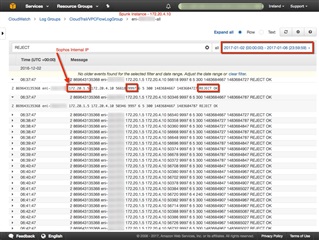
However, this isn't working for the Splunk instance - when I try to SSH from Frankfurt to the Splunk instance in Ireland, the traffic appears go through the Ireland Sophos Firewall but not being received:
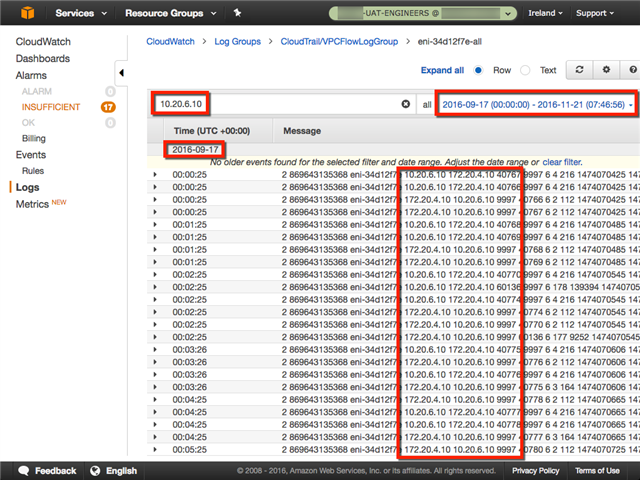
I have also verified that the VPC Flow logs show access from 10.20.6.10 before when I was using OpenSwan but not after switching to Sophos UTM 9 site-to-site VPN for AWS VPC.
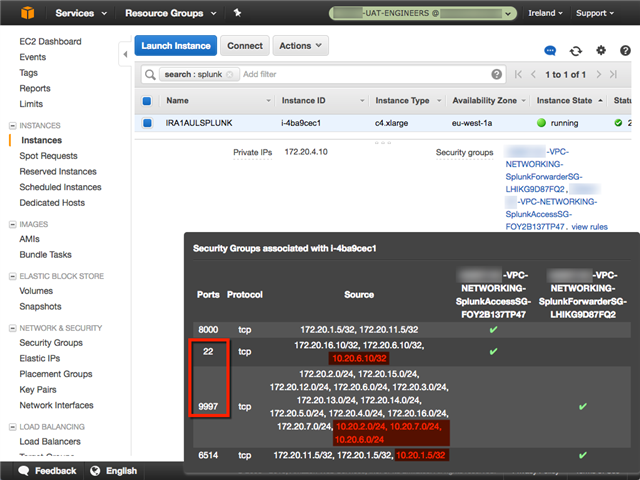
The Security Group on the target Splunk instance is configured correctly (I think):
What am I missing?
This thread was automatically locked due to age.