Hello,
I cannot browse webpages when my SSL VPN is connected.
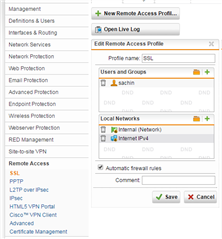
In remote access -> SSL -> local networks, there is included any network.
Should I use config-file settings in SSL VPN Client Settings?
Here are logs if that helps solve the problem:
Sun Sep 18 04:32:01 2016 OpenVPN 2.3.0 i686-w64-mingw32 [SSL (OpenSSL)] [LZO] [IPv6] built on Mar 23 2015
Enter Management Password:
Sun Sep 18 04:32:01 2016 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
Sun Sep 18 04:32:01 2016 Need hold release from management interface, waiting...
Sun Sep 18 04:32:02 2016 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
Sun Sep 18 04:32:02 2016 MANAGEMENT: CMD 'state on'
Sun Sep 18 04:32:02 2016 MANAGEMENT: CMD 'log all on'
Sun Sep 18 04:32:02 2016 MANAGEMENT: CMD 'hold off'
Sun Sep 18 04:32:02 2016 MANAGEMENT: CMD 'hold release'
Sun Sep 18 04:32:11 2016 MANAGEMENT: CMD 'username "Auth" "xxx"'
Sun Sep 18 04:32:11 2016 MANAGEMENT: CMD 'password [...]'
Sun Sep 18 04:32:11 2016 WARNING: Make sure you understand the semantics of --tls-remote before using it (see the man page).
Sun Sep 18 04:32:11 2016 NOTE: OpenVPN 2.1 requires '--script-security 2' or higher to call user-defined scripts or executables
Sun Sep 18 04:32:12 2016 Socket Buffers: R=[65536->65536] S=[65536->65536]
Sun Sep 18 04:32:12 2016 Attempting to establish TCP connection with [AF_INET]xxx:8833 [nonblock]
Sun Sep 18 04:32:12 2016 MANAGEMENT: >STATE:1474162332,TCP_CONNECT,,,
Sun Sep 18 04:32:13 2016 TCP connection established with [AF_INET]xxx:8833
Sun Sep 18 04:32:13 2016 TCPv4_CLIENT link local: [undef]
Sun Sep 18 04:32:13 2016 TCPv4_CLIENT link remote: [AF_INET]xxx:8833
Sun Sep 18 04:32:13 2016 MANAGEMENT: >STATE:1474162333,WAIT,,,
Sun Sep 18 04:32:13 2016 MANAGEMENT: >STATE:1474162333,AUTH,,,
Sun Sep 18 04:32:13 2016 TLS: Initial packet from [AF_INET]xxx:8833, sid=11327cb6 cee03a
Sun Sep 18 04:32:13 2016 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Sun Sep 18 04:32:13 2016 VERIFY OK: depth=1, C=xx, L=xx, O=xx, CN=xxx VPN CA, emailAddress=xxx
Sun Sep 18 04:32:13 2016 VERIFY X509NAME OK: C=xx, L=xx, O=xx, CN=xxx_SOPHOS_1, emailAddress=xxx
Sun Sep 18 04:32:13 2016 VERIFY OK: depth=0, C=xx, L=xx, O=xxx, CN=xxx_SOPHOS_1, emailAddress=xxx
Sun Sep 18 04:32:13 2016 Data Channel Encrypt: Cipher 'DES-EDE3-CBC' initialized with 192 bit key
Sun Sep 18 04:32:13 2016 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sun Sep 18 04:32:13 2016 Data Channel Decrypt: Cipher 'DES-EDE3-CBC' initialized with 192 bit key
Sun Sep 18 04:32:13 2016 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sun Sep 18 04:32:13 2016 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 2048 bit RSA
Sun Sep 18 04:32:13 2016 [xxx_SOPHOS_1] Peer Connection Initiated with [AF_INET]xxx:8833
Sun Sep 18 04:32:14 2016 MANAGEMENT: >STATE:1474162334,GET_CONFIG,,,
Sun Sep 18 04:32:15 2016 SENT CONTROL [xxx_SOPHOS_1]: 'PUSH_REQUEST' (status=1)
Sun Sep 18 04:32:15 2016 PUSH: Received control message: 'PUSH_REPLY,route-gateway 10.xxx.2.1,route-gateway 10.xxx.2.1,topology subnet,ping 10,ping-restart 120,redirect-gateway def1,dhcp-option DNS xxx,dhcp-option DNS 8.8.8.8,ifconfig 10.xxx.2.2 255.255.255.0'
Sun Sep 18 04:32:15 2016 OPTIONS IMPORT: timers and/or timeouts modified
Sun Sep 18 04:32:15 2016 OPTIONS IMPORT: --ifconfig/up options modified
Sun Sep 18 04:32:15 2016 OPTIONS IMPORT: route options modified
Sun Sep 18 04:32:15 2016 OPTIONS IMPORT: route-related options modified
Sun Sep 18 04:32:15 2016 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Sun Sep 18 04:32:15 2016 ROUTE_GATEWAY 192.168.1.1/255.255.255.0 I=5 HWADDR=xxx
Sun Sep 18 04:32:15 2016 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Sun Sep 18 04:32:15 2016 MANAGEMENT: >STATE:1474162335,ASSIGN_IP,,10.xx.2.2,
Sun Sep 18 04:32:15 2016 open_tun, tt->ipv6=0
Sun Sep 18 04:32:15 2016 TAP-WIN32 device [Ethernet 2] opened: \\.\Global\{xx-B74E-4C9E-8F09-23F7247681xx}.tap
Sun Sep 18 04:32:15 2016 TAP-Windows Driver Version 9.20
Sun Sep 18 04:32:15 2016 Set TAP-Windows TUN subnet mode network/local/netmask = 10.xx.2.0/10.xx.2.2/255.255.255.0 [SUCCEEDED]
Sun Sep 18 04:32:15 2016 Notified TAP-Windows driver to set a DHCP IP/netmask of 10.xx.2.2/255.255.255.0 on interface {xx-B74E-4C9E-8F09-23F7247681xx} [DHCP-serv: 10.xx.2.254, lease-time: 31536000]
Sun Sep 18 04:32:15 2016 NOTE: FlushIpNetTable failed on interface [2] {xx-B74E-4C9E-8F09-23F7247681xx} (status=5) : Access is denied.
Sun Sep 18 04:32:19 2016 TEST ROUTES: 2/2 succeeded len=1 ret=1 a=0 u/d=up
Sun Sep 18 04:32:19 2016 C:\WINDOWS\system32\route.exe ADD xx MASK 255.255.255.255 192.168.1.1
Sun Sep 18 04:32:19 2016 Route addition via service succeeded
Sun Sep 18 04:32:19 2016 C:\WINDOWS\system32\route.exe ADD 0.0.0.0 MASK 128.0.0.0 10.xx.2.1
Sun Sep 18 04:32:19 2016 Route addition via service succeeded
Sun Sep 18 04:32:19 2016 C:\WINDOWS\system32\route.exe ADD 128.0.0.0 MASK 128.0.0.0 10.xx.2.1
Sun Sep 18 04:32:19 2016 Route addition via service succeeded
Sun Sep 18 04:32:19 2016 MANAGEMENT: >STATE:1474162339,ADD_ROUTES,,,
Sun Sep 18 04:32:19 2016 C:\WINDOWS\system32\route.exe ADD xxx MASK 255.255.255.255 192.168.1.1
Sun Sep 18 04:32:19 2016 ROUTE: route addition failed using service: The object already exists. [status=5010 if_index=5]
Sun Sep 18 04:32:19 2016 Route addition via service failed
Sun Sep 18 04:32:19 2016 Initialization Sequence Completed
Sun Sep 18 04:32:19 2016 MANAGEMENT: >STATE:1474162339,CONNECTED,SUCCESS,10.xx.2.2,xxx
This thread was automatically locked due to age.