Hi!
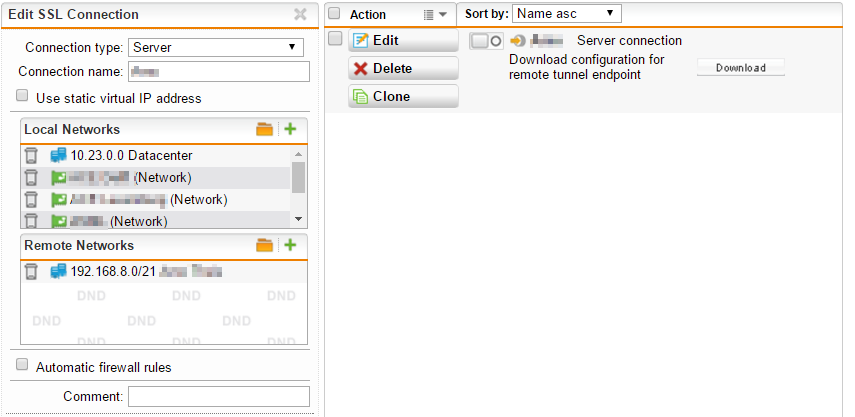
I created a Remote Access SSL VPN Profile, with a masquerade rule (VPN Pool (SSL) --> Internal). I'm using an Asus router on the remote site.
The Asus router has a builtin VPN client and it was pretty easy to configure. The Asus router connects without any problems and, thanks to the masquerade rule, the clients on the remote subnet (behind the Asus router) can connect with the clients on the internal subnet (behind the Sophos UTM) without any problems.
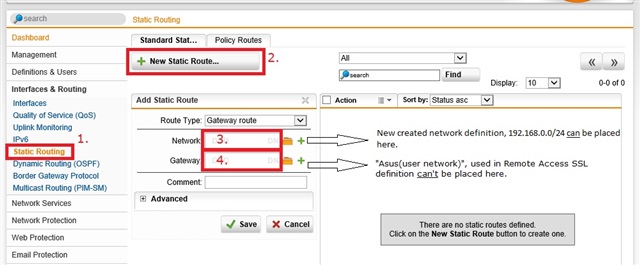
I would like to connect from an internal client to a host on the remote subnet (behind the Asus router). Because I use the default VPN Pool (SSL) the Asus router SSL VPN client is on IP-adres 10.242.2.2. I can connect to the Asus web interface (on 10.242.2.2) from a client on the internal subnet. I can't connect to a host on the 192.168.0.0/24 subnet.
Internal subnet - SOPHOS UTM <------------------ ASUS Router builtin (OpenVPN client) - Subnet on remote site (192.168.0.0/24)
Regards!
Jeroen
This thread was automatically locked due to age.