Hi all,
I've recently replaced my TMG 2010 with the latest UTM 9 software appliance on a vm (ESXi).
I must say, the WebAdmin is a treat, a wealth of options & features, with a bit of a learning curve as well, but loving it :)
The LAN setup (private interface) and WAN setup (public interface) is identical as with my earlier TMG setup.
After porting the firewall & NAT rules, everything seems to work fine, very impressed with all the protection & reporting features.
The only thing that seems problematic so far is the remote access via a VPN connection.
At the moment I'm using the rather insecure PPTP (will build a L2TP/IPsec / SSL VPN later on).
This connection always worked fine via the TMG, also rocksolid in keeping the connection alive, no disconnects whatsoever.
But now with UTM 9, when the line (VDSL2 100d/10u) is heavily in use, for example an FTP connection which saturates the line,
the VPN connection will be disconnected in seconds after the heavy traffic starts, this was never the case with the TMG.
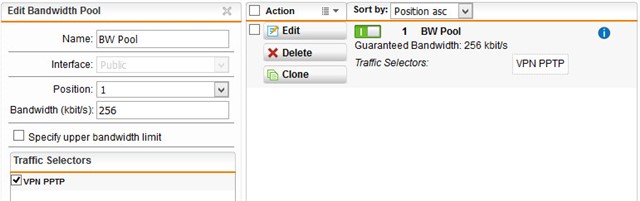
I've already tried giving the VPN traffic a guaranteed bandwidth via QOS, but same thing keeps happening.
Any ideas to strengthen the VPN connection in UTM in order to prevent these disconnect and make it more robust / resilient?
Thanks for any tips!
Paul.
This thread was automatically locked due to age.