I would like to set up a VPN at the company office, but limit access to only selected user accounts on our Windows Server. I have successfully created the Authentication Server in Definitions and Users, Authentication Services. The Test server settings and Authenticate example user Tests both pass.
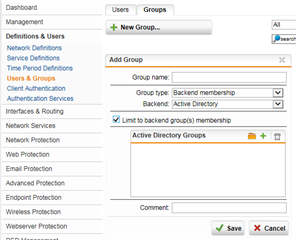
When configuring a VPN, I can choose "Active Directory Users" for Users and Groups, but I cannot choose only a subset of those users.
What are the steps necessary to have a selectable list of active directory users for my VPN services? (Step by step, please.)
Will I be violating Bob's Rulz #6 if I allow users to use their Windows passwords to authenticate to the VPN?
This thread was automatically locked due to age.