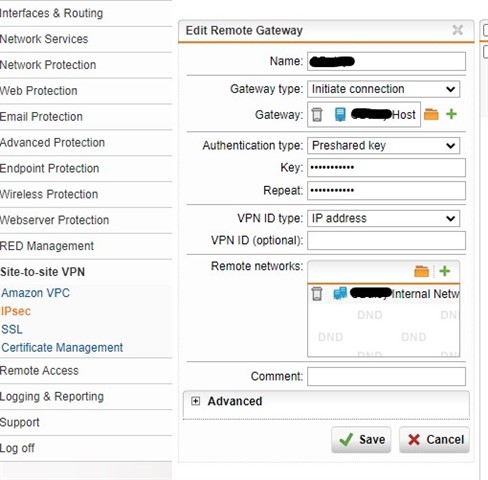
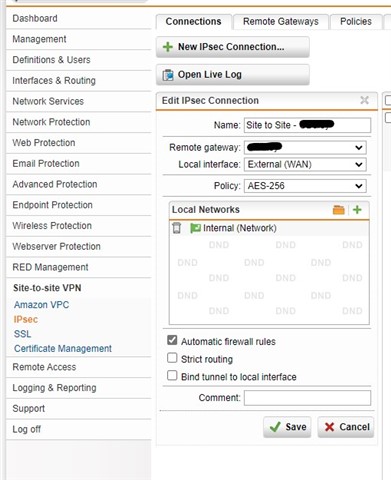
I'm trying to implement the configuration, but it doesn't work:
support.sophos.com/.../KB-000036832
I followed the instructions exactly point by point.
1. Error message:
"we require peer to have ID 'IP Adress', but peer declares 'FQDN'
I changed on Side A /Advanced/Preshared KeySettings/ to VPN-ID-Typ: Hostname and VPN-ID to FQDN
the error message no longer comes, but new error messages:
Side B: ignoring informational payload, type INVALID_ID_INFORMATION and ignoring informational payload, type INVALID_MESSAGE_ID
Side A:
sending encrypted notification INVALID_ID_INFORMATION to "IP Address"
what am I doing wrong?
This thread was automatically locked due to age.