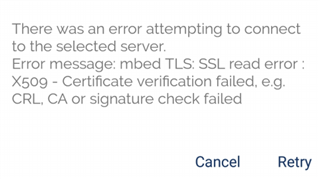
Prior to an OpenVPN for Android update, all of our mobile devices could connect to our Sophos UTM 9 SSL VPN without error. Now there seems to be a problem because the new version of OpenVPN does not support the md5 authentication algorithm, which I believe our CA is using.
What we did up to this point was go into Remote Access SSL -> Advanced and changed our authentication algorithm from md5 to SHA2 256 and applied the change. Then went to the user portal and downloaded the config. Then imported the config into OpenVPN on the android devices.
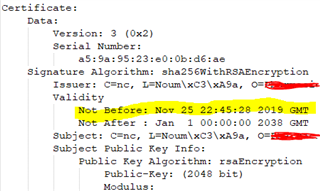
We are now receiving the error "CA signature digest algorithm too weak". I believe that is because our VPN Signing CA is still using md5. At least that is what I see in the PEM file.
My question is if I choose to Regenerate Signing CA will our Signing CA then use the SHA2 256 algorithm? Would I be better off creating a new CA instead?
I gather that regenerating our signing CA will require everyone to download an updated config file, but will it cause any problems with any existing site-to-site VPN entries we have?
This thread was automatically locked due to age.