Hi there
Trying to setup an inbound NAT rule from 0.0.0.0/0 , to a server sitting inside of a VPC inside AWS on a private subnet.
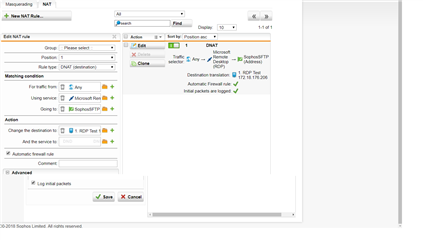
I have setup the NAT rule as below and can see the traffic passing. The VPC routing inside of the VPC is set to direct traffic to the Network interface of the Sophos for any traffic that is 0.0.0.0/0
The issue is the server I have is a SFTP server, and it blocks traffic from specific IP's on repeated failed attempts e.g. if someone tries to brute force the SFTP server it will blacklist the IP address. Therefore I need the firewall to not translate inbound traffic and retain the original WAN IP addresses that are trying to connect to the Sophos firewall. Otherwise the SFTP will block the IP address of the Sophos firewall IP and nobody will be able to access to the SFTP Server (Because the SFTP server would see only the translated IP address of the Sophos).
Is it possible to do a NAT whilst retaining the original IP of the person sending traffic into our SFTP server?
This thread was automatically locked due to age.