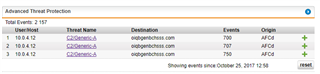
Since not quite the first of the month, we've had a very interesting and chronic trigger on our firewall...
I have been continually running different malware/antivirus scans on the server and resetting to see if I have cleared off the problem, but to no avail. I know it's possible these could be false positives, but it just seems so odd that there's so dang *many* triggers, up in the thousands per day. I've Googled just about everything I can think of to try to find more information, to try to figure out if indeed we have an infection or if this is a wild goose chase, but I'm not 100% certain yet. Thankfully, this means that any of the packets being sent to that destination are being dropped, so if it is a bad site, it's not as bad as it could be... but I would prefer to get the triggers to stop altogether, rather than just resetting every time I run a scan. There are two destination IPs connected to this host - 208.67.222.222 and 208.67.220.220. A cursory Google will show that both of these are OpenVPN server addresses. We happen to use the VPN built in to the Firewall, but we've been using that for awhile now and it never triggered anything like this.
Has anybody else seen anything like this? Any other thoughts or suggestions? I can only run the same malware and virus scans so many times before it gets old.
This thread was automatically locked due to age.