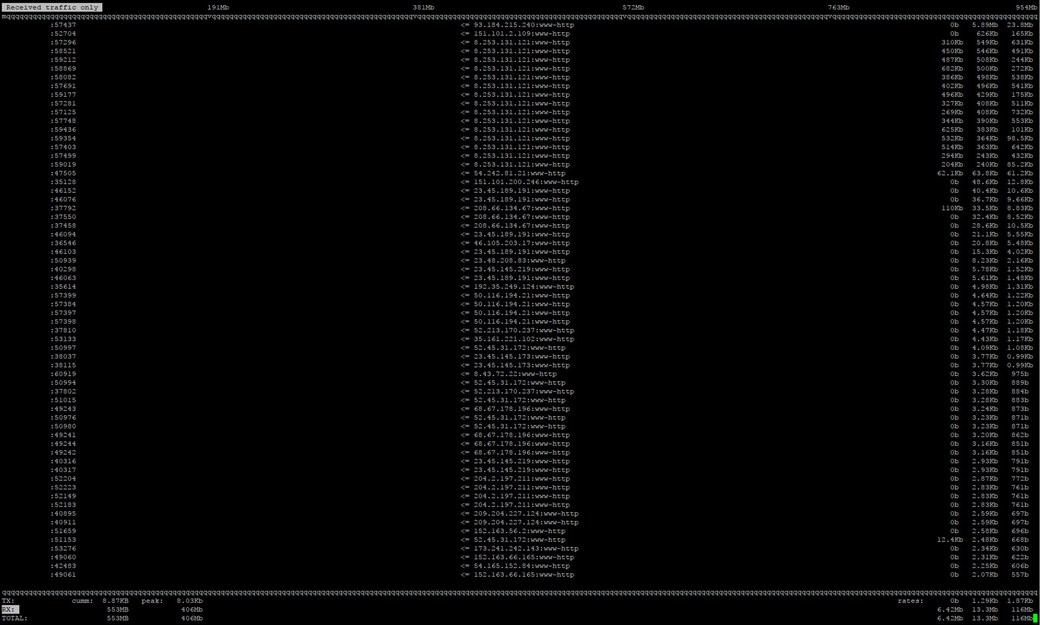
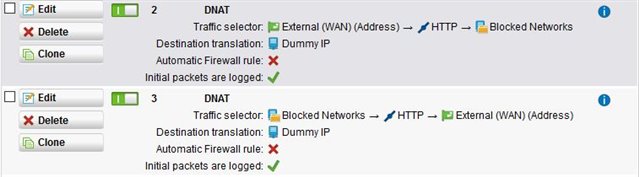
Our External WAN is being bombarded by Gigabits of incoming WWW-HTTP traffic that I can not drop with Firewall Rules.
I've looked through Country Blocking Exceptions, Automatic NAT Rules, Proxies (Web, SMTP, Application Control, VPNs, etc) and unable to locate any exceptions that may be allowing this traffic that is causing high latency and congestion on our External WAN. Our RED Networks are especially affected.
This bombardment of WWW-HTTP traffic began within the past two days and is constantly occurring. Furthermore, the IP addresses that are causing this traffic are also showing up in the IPS logs and causing the following alerts
2017:10:12-08:22:39 sophos snort[28745]: S5: Session exceeded configured max bytes to queue 1048576 using 1055824 bytes (client queue). blanked 56127 --> 8.249.99.254 80 (0) : LWstate 0x9 LWFlags 0x6007
2017:10:12-08:23:00 sophos snort[28745]: S5: Session exceeded configured max bytes to queue 1048576 using 1053826 bytes (client queue). blanked 56407 --> 8.249.99.254 80 (0) : LWstate 0x9 LWFlags 0x6007
2017:10:12-08:23:10 sophos snort[28739]: S5: Session exceeded configured max bytes to queue 1048576 using 1052186 bytes (client queue). blanked 33135 --> 67.24.105.254 80 (0) : LWstate 0x9 LWFlags 0x6007
2017:10:12-08:23:17 sophos snort[28745]: S5: Session exceeded configured max bytes to queue 1048576 using 1058162 bytes (client queue). blanked 56443 --> 8.249.99.254 80 (0) : LWstate 0x9 LWFlags 0x6007
2017:10:12-08:23:20 sophos snort[28739]: S5: Session exceeded configured max bytes to queue 1048576 using 1050082 bytes (client queue). blanked 33174 --> 67.24.105.254 80 (0) : LWstate 0x9 LWFlags 0x6007
2017:10:12-08:23:28 sophos snort[28739]: S5: Session exceeded configured max bytes to queue 1048576 using 1052730 bytes (client queue). blanked --> 67.24.105.254 80 (0) : LWstate 0x9 LWFlags 0x6007
Here's are some IFTOP results of the traffic:
Any insight on why I can't drop this traffic would be appreciated.
Thanks!
This thread was automatically locked due to age.