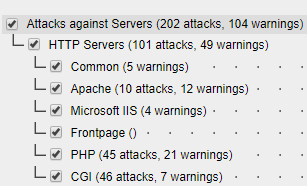
I'm looking at either a supplement or alternative to fail2ban that we have already running on a publicly exposed Apache server. I can see that under IPS setting on the Sophos UTM, there are attack patterns relevant to HTTP Servers/Apache:
We have been adding fail2ban jails to our Apache server in response to attacks that occur, but I'm wondering if these IPS attack patterns might offer a less reactive approach to the problem...
For example: We noticed a Russian IP sending thousands of HTTP GET/POST requests to the server, so we created a fail2ban jail to ban any IP that sends a certain number of requests over a 30 second period. This works, but seems patchwork.
Would the scenario described above be a relevant use-case for Sophos IPS? Is there a way I can see what patterns "Attacks against Servers > HTTP Servers > Apache" is tracking? Maybe this is concealed so that attackers can't work around them?
Thanks,
Ryan
This thread was automatically locked due to age.