I have been reading through Rulz and this earlier post trying to get my blackhole/null route working with DNAT since my firewall rules were not (as explained by Rulz). From the latter link, BAlfson said the following is a valid DNAT configuration:
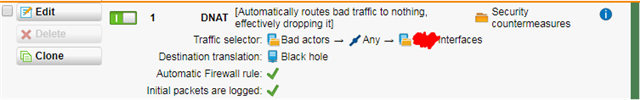
"DNAT : {group of bad IPs} -> Any -> {group of WAN (Address) objects} : to {non-existent IP}"
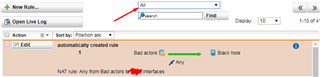
So I changed my configuration to look just like that:
- "Bad actors" contains a variety of IP address Host objects,
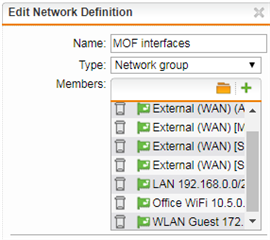
- "x Interfaces" contains a variety of * (Address) network objects
- and "Black hole" is another Host object pointing to an invalid IP, which in my mind completes the null route creation
As you can see, I've told it to create an automatic firewall rule, and verified it is the first firewall rule to be processed after toggling all other NAT rules off and on again:
As a test, I added NPR.org's IP address to Bad actors, and then tried visiting their website via that same IP (HTTP & S) and it still loaded fine.
From what I can tell, there are no exceptions in place for my machine.
Am I contradicting the DNAT by adding both my external WAN interface IPs and the LAN interface IPs?
EDIT: disregard above question, I've tried only having external interfaces as well as just the 1 external interface (address) object with no change.
What should I try next?
This thread was automatically locked due to age.