Hi!
UTM9 (Release 9.502-4 ) is informing me that some clients are infected with malware. I now blocked these clients using a firewall rule (Network Protection >> Firewall).
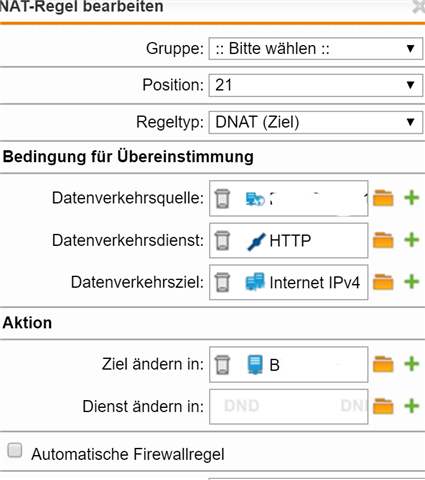
I would instead like to redirect all requests from these clients to an internal webserver, showing them an information message that they got blocked. I cannot redirect clients at the firewall, only allow or deny traffic. How do I do it?
Thanks in advance! Simon
PS: My first post here, sorry if I did something wrong. :)
This thread was automatically locked due to age.