I couldn't find a specific answer to this. So, sorry in advance if it is already answered.
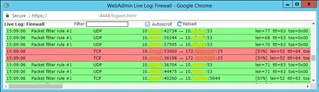
Our UTM is dropping outbound TCP port 25 without any information on where the DROP is defined (logs don't have DEFAULT DROP, etc after time, before protocol). I do not have any automatic rules defined, all firewall rules have been manually created. I put a test rule at the top allowing TCP port 25 from a specific local IP to a specific external IP, no dice, initial SYN packet dropped. I even created a new service definition for TCP/UDP port 25 and set the rule to log initial packets. No logged packet in the logs, just the log about the packet being dropped by some unknown rule. Something is filtering the packets before they get to the defined (user or auto) firewall rules.
I read about SMTP proxy creating a hidden rule. Our UTM is only licensed for Network and Webserver Protection. We want to send SMTP emails from specific internal hosts to specific external hosts.
This thread was automatically locked due to age.