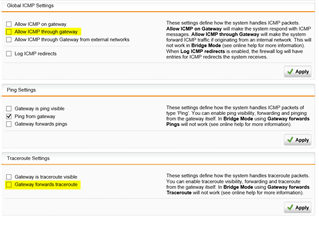
I setup a DMZ on a separate physical interface on a SG330; however, I can still ping hosts on all our internal networks. The only way for me to get this to stop is to disable both "Global ICMP Settings" and "Traceroute Settings" under the Network Protection > Firewall > ICMP. Disabling only one option still allowed PING to traverse the interfaces. It bugs me that this is the case. Is this normal?
Also, I attempted to create a firewall rule like DMZ Network> PING, PING6, Any, All Protocols > Internal Interface Network: Deny which had no affect whatsoever....is that normal? I thought having this rule would let me block pinging, etc. between the two networks and leave the others alone, but nope.
Also, maybe my lack of experience, but our traffic flows similar to this...
Internet > Layer 3 switch > firewall > same layer 3 switch...
I wouldn't think that setup would matter since all traffic on the DMZ must pass through it's default gateway which is the SG330. The default gateway for all the other subnets/vlans is the layer 3 switch.
Anyone know why the SG doesn't block ping between interfaces when they are separate networks? Have I totally missed the point on how to configure a DMZ with the SG?
This thread was automatically locked due to age.