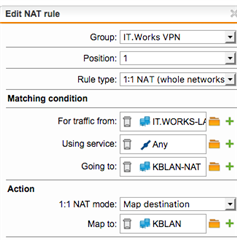
How does 1:1 NAT work in conjunction with WAF?
Scenario:
You have a host that has multiple services on it eg SMTP, POP3, IMAP, FTP, SSH & HTTP/S which you want to expose to the web.
Now the WAF can proxy the HTTP/S so no NAT rule is needed. But what about the rest?
Should it be a multiple DNAT or a single 1:1 NAT?
This thread was automatically locked due to age.