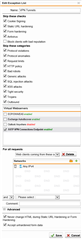
I have a few HTTPS sites successfully published through my UTM Firewall (mostly Exchange Admin Console/Outlook Web Access).
I'm now trying to set up another application, using a different domain name, but the Web Application Firewall log is reporting the following error:
I've created firewall rule to allow the traffic (with logging enabled), but nothing is showing up in the firewall logs.
Is there any way I can configure UTM not to scan traffic bound for this particular domain/URL, and just pass it straight through? Obviously, I can't create a NAT rule, as it will break the other HTTPS sites currently working through the UTM.
Or, is there some way I can disable this 'prefetch' attempt that UTM is attempting?
Many thanks
This thread was automatically locked due to age.