Hi,
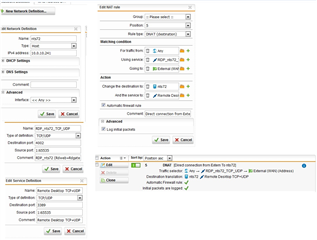
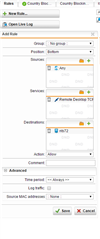
We have a DNAT rule that allow us to access our server with RDP from internet with different port number, the rule working correctly, but in the logs we can see lots of drop UDP connections from the the IP address and port number that we try to access the server with RDP.
what are these UDP packages? why should the we see incoming UDP packages at all?
This thread was automatically locked due to age.