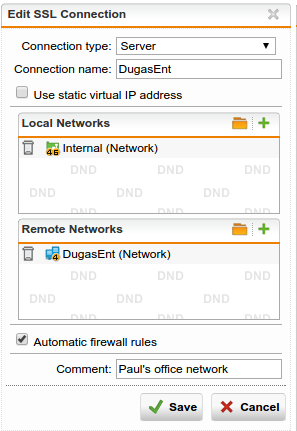
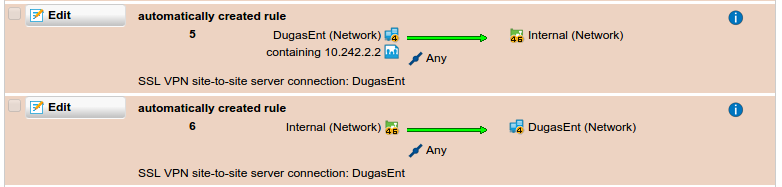
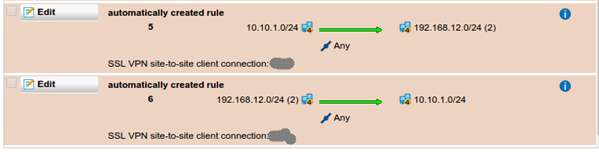
The automatically-generated firewall rules for a site-to-site SSL VPN connection allow traffic to/from the remote network as well as the IP address assigned to the tunnel; i.e. 10.242.2.x or something like that. I need to setup rules along the same lines but tighter on the allowed protocols but I'm not seeing an automatically created host object for that 10.242.2.x address. I got bit by this when I disabled the automatic rule and added one of my own that only listed the remote subnet. The remote firewall is another UTM that's running the transparent firewall so all the HTTP traffic ends up coming from the remote firewall's SSL tunnel address - that 10.242.2.x address. Took a little head-scratching to figure that out.
Is there a way to predict the IP assigned to that tunnel so I can include it in the firewall rules like the automatically generated rules do?
This thread was automatically locked due to age.