Hi,
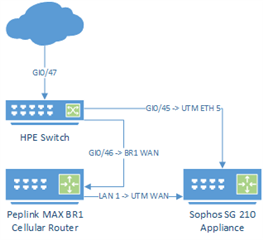
I'm looking for some guidance / advice / help in a deployment we have. We have an SG 210 configured as shown in the diagram attached; I think that will be the easiest way of showing the setup.
We have the Peplink MAX BR1 above the UTM which serves as a Cellular backup should the cable connection go down. As soon as the WAN connection drops, the Cellular kicks in and everyone at the office stays online and hardly even notices that anything happened. This device is assigned their primary IP address and also has a dynamic cellular IP as the backup. All traffic going to the primary IP is nat'd to the WAN interface of the UTM. To accomplish that the internal IP of the BR1 is 172.16.100.254 and the WAN IP of the UTM is 172.16.100.253 with it's default GW being the BR1. This works perfectly, no problems at all - it allows us to have the failover and keep the UTM handling all the FW rules and web filtering etc.
We then have that second connection from the switch going directly into ETH 5 on the UTM and it's assigned one of their other public IP addresses. We can verify traffic hit's this interface with no problem at all as we see all that activity in the logs, so we know that's working. Here's where things start to fail on us.
The entire reason for the second IP was for the L2TP over IPsec VPN. This doesn't work behind a nat'd router so we needed to bypass the BR1 and dedicate this IP for VPN traffic. We've setup about 5 of these without any trouble at all but they are all using the default WAN interface. We simply cannot get this to work. We see the traffic come in, but it appears as though the return traffic is going back out of the primary WAN's gateway. So in essence, traffic comes in on (as an example) their second / VPN IP which we'll say is 1.1.1.2 but then goes straight back out their primary IP 1.1.1.1 - needless to say the VPN never connects.
I have tried to add static routes, gateway routes, policy routes, MASQ rules and anything else that I can find and think of but nothing makes any difference. Traffic coming in on 1.1.1.2 will return from 1.1.1.1
I am hoping I'm missing something obvious. Has anyone faced similar issues or have a similar setup working and could shed some light on what we're doing wrong? At this point any suggestions or help would be greatly appreciated.
If I haven't made anything clear please let me know and I'll try to clarify further. We're running the latest firmware and this is a single SG 210 - no HA in this deployment.
Thank you in advance!
This thread was automatically locked due to age.