Hello,
I've recently come across a problem that in my eyes makes no sense, I have been trying to get DNAT to work with a new DMZ server.
We have an additional server in the DMZ already, fully functioning. I've tried copying every single rule and configuration from that one, however it is not that simple.
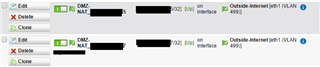
I first created the additional interface which will be the external IP-address of the server. (x.x.x.x/32).
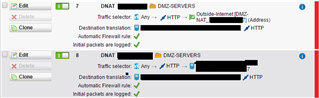
Secondly, I created DNAT for the DMZ: Any->Port 80->External-IP of Additional Interface -> Change to: internal private IP of DMZ-server -> same port number as in first step (80).
When trying to access this IP using any webbrowser, it returns no answer, nothing at all.
I can ping the external IP-address of the physical external interface, but not the additional interface that I created for the DMZ public IP.
According to the WebGUI, the additional interface and the physical interface itself are up and running.
Hopefully you can help me resolve this :)
Best regards,
Eric
This thread was automatically locked due to age.