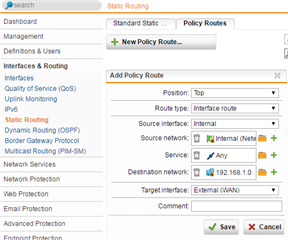
I have 4 internal lans:
LAN A = 10.1.1.0/24
LAN B = 10.1.2.0/24
LAN C = 10.1.3.0/24
LAN D = 10.1.4.0/24
I have 3 WAN's:
WAN A = 1.1.1.1
WAN B = 2.2.2.2
WAN C = 3.3.3.1/29 (goes to 192.168.1.0/24 via 3.3.3.2/29)
I want to nat all LAN's to various WAN's
LAN A >>> WAN A (using Masquerade)
LAN B >>> WAN B (using Masquerade)
LAN C >>> WAN C (using Masquerade)
I want LAN D >>> WAN C (using Masquerade)
However, I also want LAN A to nat to WAN C when a user tries to get to 192.168.1.0/24
Bear in mind that LAN A already has a masq rule to WAN A
This thread was automatically locked due to age.