I've been working for a few weeks now porting over config & function from Cisco ASA and PIX to our new Sophos SG330 running UTM v9.406-3.
We have a /27 block of public IPs.
I've been doing a lot of reading today about NAT on UTM. I've got an interface on the SG 330 labelled as OUTSIDE.
I have one of my public IPs bound to OUTSIDE.
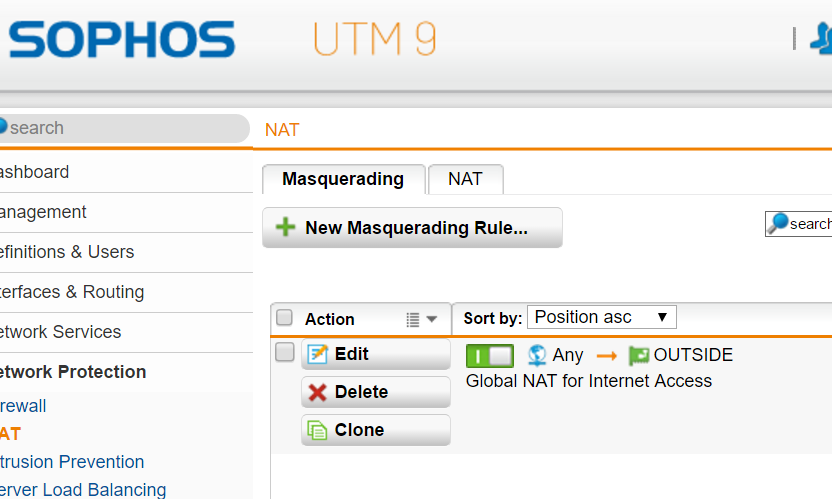
On this Masquerading tab, OUTSIDE is set as what I would call the "global" or "overload" NAT - everyone inside accessing the Internet appears to come from this one IP.
I guess in the context of UTM, you could also call that Many-To-One SNAT.
I have the rest of my public IPs setup as Additional Addresses on OUTSIDE.
I understand that I can use DNAT for inbound from internet to PublicIP thru UTM to PrivateIP.
Then I can use SNAT so that PrivateIP thru UTM shows up to the world as PublicIP - instead of the "global" or "overload" NAT defined in Masquerading.
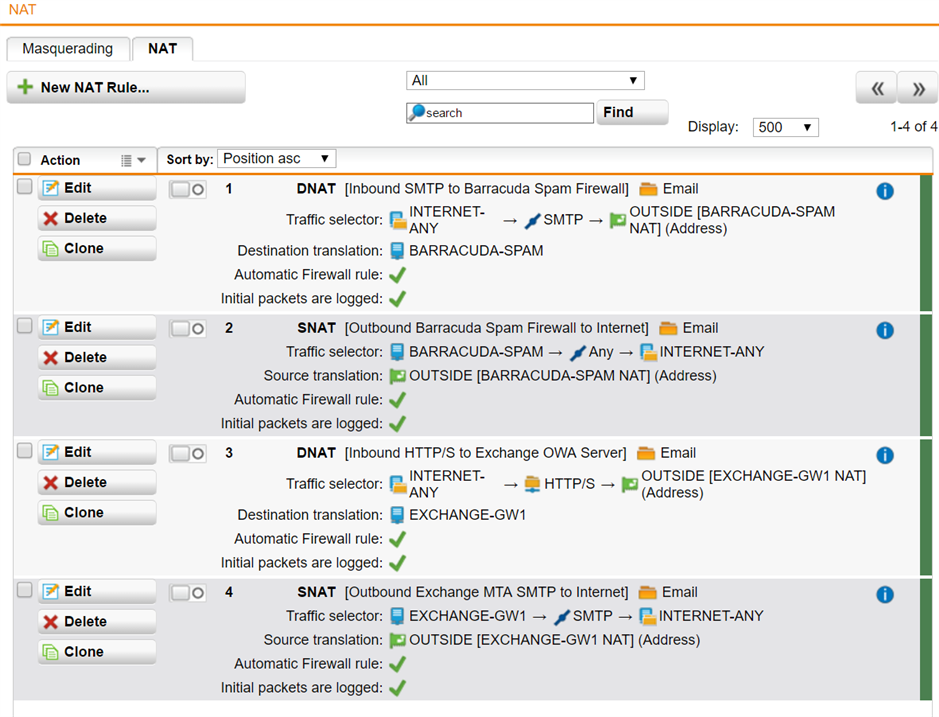
I think I have it setup correctly for:
DNAT: Inbound SMTP to public IP assigned to Barracuda Spam Firewall's private IP.
SNAT: Outbound all protocols from Barracuda's private IP to the internet via that same public IP.
DNAT: Inbound HTTP/S to public IP assigned to Exchange server private IP.
SNAT: Outbound SMTP from Exchange server private IP.
See screen captures:
Now, based upon the above configuration, I think I can draw the following conclusions:
1. All inbound traffic from the Internet to the Barracuda's public IP will be blocked, except SMTP which will be forwarded in to the Barracuda's private IP.
2. All outbound traffic from the Barracuda's private IP to the Internet is allowed, and it will show up as sourced from the Barracuda's public IP.
3. All inbound traffic from the Internet to the Exchange server's public IP will be blocked, except HTTP/S which will be forwarded in to the Exchange server's private IP.
4. All outbound traffic from the Exchange server's private IP to the Internet will appear to come from the OUTSIDE IP as defined in Masquerading, EXCEPT SMTP which will appear to come from the Exchange server's public IP.
Are my conclusions correct?
Thank you!
This thread was automatically locked due to age.