Hi,
I'm setting up an UTM-9 on an sg210 and I'm stumped by a really simple question:
What is the difference between setting a single IP and setting a network range in the destination field of a firewall rule?
I'd say the latter rule matches each and every destination ip in the configured network, but that's not how the UTM-9 appears to beahve. My setup:
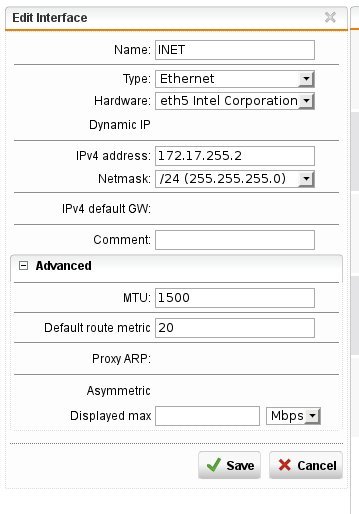
- UTM-9 is connected with a single interface with ip/mask 192.168.1.2/24 to a switch.
- Not sure if this is relevant, but the default gw is configured on an other interface with ip 192.168.100.1/24.
- The only other connected host on the switch is my workstation, configured with ip 192.168.1.1/24
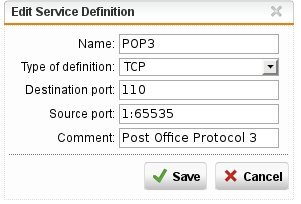
- On the UTM-9 I start a listener on 192.168.1.2:110 (with nc -v -l 192.168.1.2 110)
As expected, trying to connect from my workstation to 192.168.1.2:110 fails and the firewall log shows that the connection was dropped by the default rule.
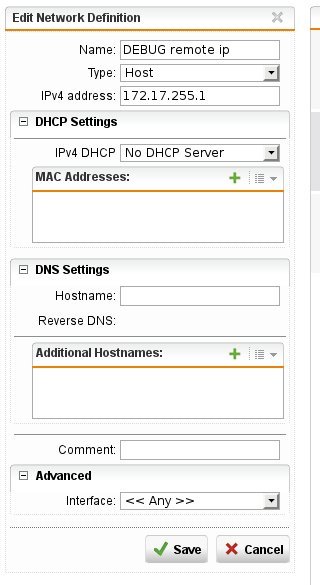
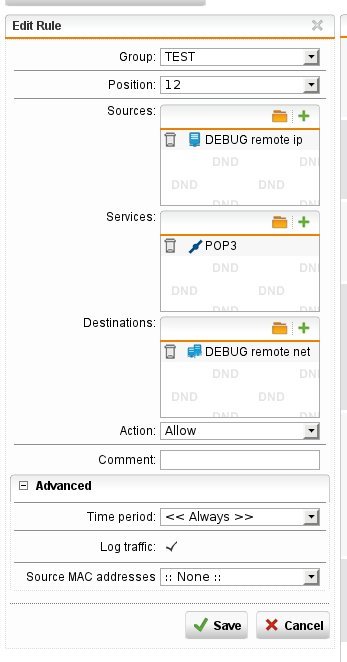
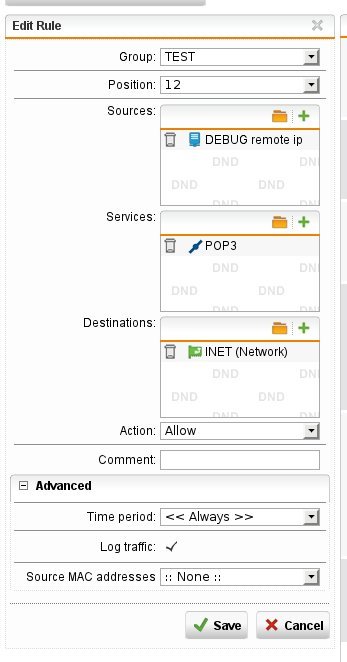
Now I add a firewall rule to allow traffic from 192.168.1.1 to 192.168.1.2 port 110: I can establish the connection, as expected.
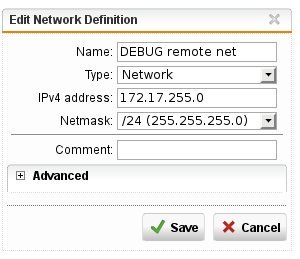
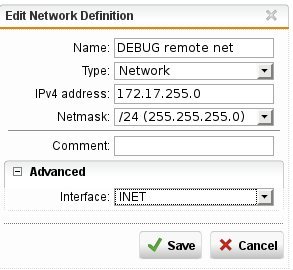
Now I replace the target ip with the interface network 192.168.1.2/24 in the firewall rule and restart the 'nc' tool: I'm not able to connect. The firewall log shows the default drop rule dropped the connection.
Could someone please explain to me, why the last step doesn't work as I hoped it would?
Thanks.
This thread was automatically locked due to age.