Here's a doozy. I have an IPSEC VPN connection with a default route such that machines on the VPN subnet will "emerge" onto the Internet from the Sophos at my main office. That's perfect, and precisely what I want.
But it only works when I run tcpdump -i br0 on the Sophos! The instant I stop tcpdump, pings no longer work.
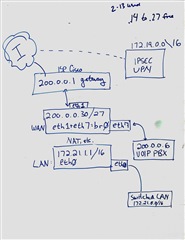
External IP on the Sophos: 200.0.0.30/27
Upstream gateway: 200.0.0.1
Bridge Interface 0 is eth1 and eth7, because eth7 is connected to a VOIP PBX device that is required to have an external public IP address, 200.0.0.6. Proxy ARP is checked (not sure why, it was recommended during setup and worked, so I haven't messed with it).
LAN is 172.21.0.0/16
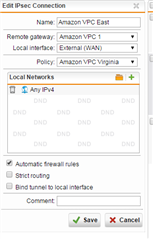
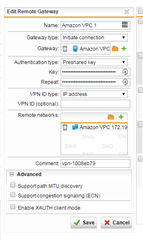
VPN is 172.19.0.0/16 and is a simple IPSEC connection to AWS VPC.
Under Additional Addresses on the Sophos, I've added 200.0.0.4 and 200.0.0.6.
I have a Masquerade rule for the VPN, so machines on the 172.19.0.0/16 VPN subnet emerge from our main router at 200.0.0.4.
Here's a picture:
Without tcpdump running:
- Ping both directions between the LAN 172.21.0.0 network and VPN 172.19.0.0 network OK
- Ping from VPN 172.19.0.0 to LAN 172.21.1.1 OK
- Ping from VPN to the Sophos external address 200.0.0.30 OK
- Ping from VPN to 200.0.0.6 (the other IP in the bridge) FAIL
- Ping from VPN to 200.0.0.1 or any other Internet address: FAIL
With tcpdump running, all pings from the VPN succeed. And it only works if I tcpdump the br0 interface.
Also notable: If I use the -p switch to disable tcpdump promiscuous mode, it doesn't work.
I'm wondering if the bridge interface is the problem, so I'm considering removing the bridge.
Is there some way I can still have the VOIP box with its external IP address, and keep it connected to eth7?
Any idea what tcpdump promiscuous mode does that "fixes" the problem? Would this indicate a packet filter or route problem somewhere?
This thread was automatically locked due to age.