Hello,
I have our remote sites set up to connect to our UTM via eth2 but users are reporting that the SIP/VoiP desk phones are not connecting and that all the remote site printers were showing as offline (Printer server is at main office).
other traffic such as web browsing and Citirx desktops are fine.
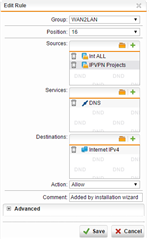
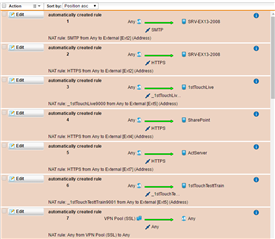
The firewall is showing that Traffic is being dropped by the default drop rule fwrule="60002":
2016:05:20-09:24:58 srv-utm1-1 ulogd[25527]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60002" initf="eth2" outitf="eth1" srcmac="a8:0c:0d:c2:a3:01" dstmac="00:1a:8c:f0:5c:e2" srcip="192.168.18.113" dstip="88.82.18.86" proto="17" length="200" tos="0x18" prec="0xa0" ttl="58" srcport="16470" dstport="35938"
2016:05:20-09:24:58 srv-utm1-1 ulogd[25527]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60002" initf="eth2" outitf="eth1" srcmac="a8:0c:0d:c2:a3:01" dstmac="00:1a:8c:f0:5c:e2" srcip="192.168.18.113" dstip="88.82.18.86" proto="17" length="200" tos="0x18" prec="0xa0" ttl="58" srcport="16470" dstport="35938"
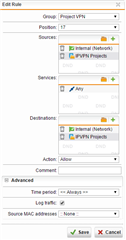
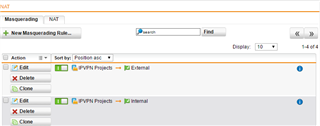
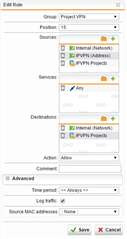
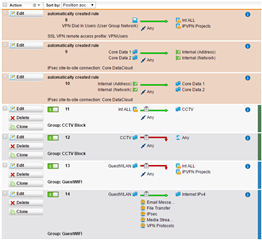
I recently had to add 2 Masquerading rule to get the remote sites connecting. The IPS log is empty for the same period.
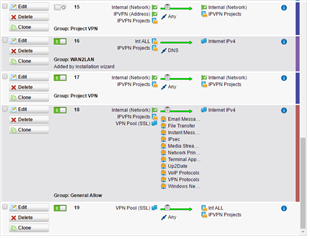
Just looking for some advice as to what could be blocking the SIP and printer traffic. the remotes sites are named IPVPN Projects in the rules.
Thanks,
Mark.
This thread was automatically locked due to age.