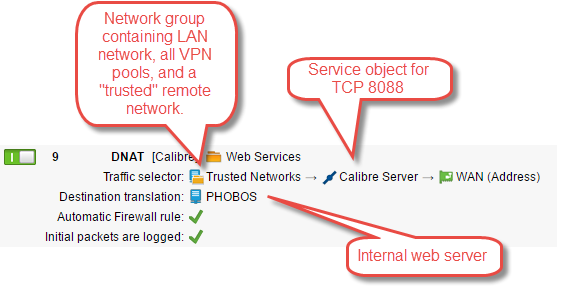
I have a small home network protected by Sophos UTM 9.3. The ISP-assigned WAN address is resolvable (using DDNS) to an FQDN--call it mydomain.com. Within this network, I have a web site running on TCP 8080. This is reachable from the WAN via a DNAT rule that translates WAN-IP:8088 to WebServer:8080 (the port change was necessary, as I already have another WAN-accessible service using port 8080).
mydomain.com:8088 -> WAN-IP --DNAT--> WebServer:8080
L2TP and SSL VPN services are set up on the UTM. With a VPN client connected, I can access internal hosts and services using IPs or local host names.
My goal is to make the above web site only accessible to the following clients/networks, but in each case be able to use http://mydomain.com:8088/ to browse the site. The networks are:
- Trusted Remote Networks
- LAN clients
- VPN clients
I created a "Trusted Networks" object containing my LAN network, the various system-generated VPN address ranges, and another remote IP range (my work network). Then I used this object to select traffic for the DNAT rule.
This works up to a point: I can browse the web site from my work IP and from the LAN, but I cannot reach it over VPN (except by using the internal IP/hostname). The firewall log shows the traffic being stopped because the source IP is not the virtual (trusted) IP of the VPN client, but the real (untrusted) IP of the remote device.
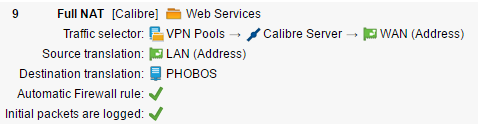
To resolve this issue, I've tried using the DNS trick discussed here to pass the internal server IP to the VPN client: https://www.sophos.com/en-us/support/knowledgebase/115191.aspx. This will work, but only when there is no port translation. I've tried using the full NAT solution, but it doesn't seem to work: again, the request appears to come NOT from the VPN pool range, but from an "untrusted" IP, so I can't select for the traffice without opening up access to *any* outside IP.
Is there any way around this situation, so that I can access the website over VPN using the same URL and port as I would from the LAN or the WAN?
This thread was automatically locked due to age.