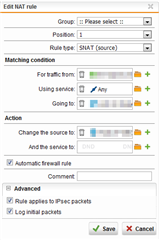
Hi, I have successfully set up an IPSEC VPN tunnel to a counter-party. However, they see my local IP address when I connect to one of their servers from my desktop (192.168.x.y). Since this will only work when they see me with our public IP i have setup a SNAT rule which i also see to be applied in the live log of the Firewall (create firewall rules automatically set). However, the other party says they don't see any packets from our end with NAT enabled. What am I doing wrong here?
This thread was automatically locked due to age.