Hi
My IDS has been reporting strange DNS queries to a malware domain every night at 12:05
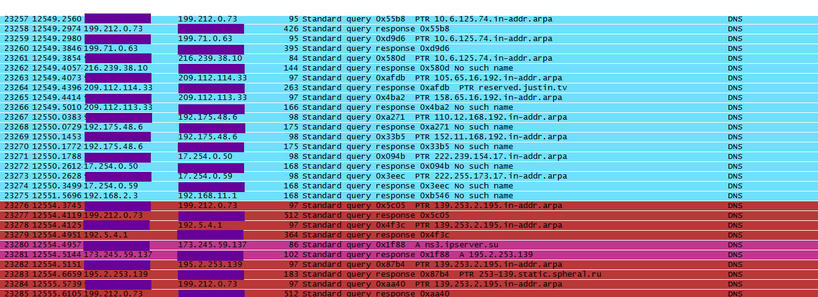
BLACKLIST DNS reverse lookup response for known malware domain spheral.ru - Win.Trojan.Glupteba
The IDS says the source is my internal DNS computer, but when I look at the logs on it, it was responding to a PTR request made from the UTM (I have the UTM forwarding to the internal DNS)
I have been trying to find if a client asking for that DNS requests.
For a test, I have disabled other networks (DMZs, phones, wifi) from using the UTM as the DNS host as a test to see if another network was causing the request. The requests still happened.
I checked the logs
Web Filtering: in that minute time frame I did not see any strange requests. The UTM proxy does its own DNS lookup for web browsing)
IDS logs: catches the internal DNS computer going out, but not the UTM making the request
Firewall logs: Show the DNS requests going out, but not the request going to the UTM (No details just A made a Dns request to B)
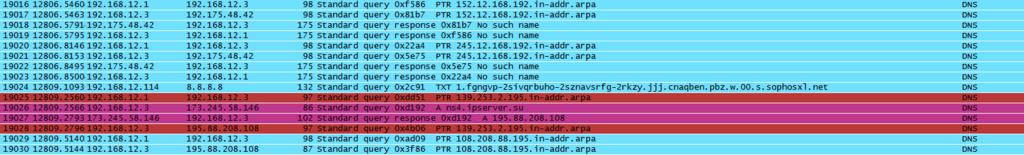
TCPDUMP: Running TCP dump over all interfaces for DNS traffic shows the initial request originating from the UTM. (tcpdump udp port 53 -nn -w capture.cap )
Web application: No request made at all around that time
So I guess my question is,
What in the UTM causes it to do PRT lookups on IP addresses, I saw it making a lot of these requests? And is there a log to see the requests made by the UTM, and why?
Thanks for any help, tonight I'm going to try disabling web filter proxy, and turn off all web application servers, see if that can help narrow down the cause.
UTM 9.213-4
This thread was automatically locked due to age.