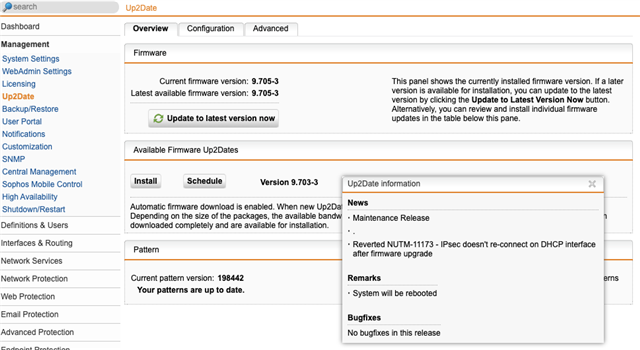
As soon as we turn on ATP on a SG450 A/S Cluster running UTM 9.705-3, the afc.log gets massively spammed with the following message:
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
2021:05:05-15:49:22 SG450 afcd[21729]: WARNING! packet already has AFC mark value (0x0000116a), replacing with 0x00001000
thus the log file files up pretty fast, here is a 30sec snapshot
SG450:/var/log # ls -lha | grep afc.log
-rw-r--r-- 1 root log 819K May 5 15:49 afc.log
SG450:/var/log # ls -lha | grep afc.log
-rw-r--r-- 1 root log 852K May 5 15:49 afc.log
SG450:/var/log # ls -lha | grep afc.log
-rw-r--r-- 1 root log 900K May 5 15:49 afc.log
SG450:/var/log # ls -lha | grep afc.log
-rw-r--r-- 1 root log 942K May 5 15:49 afc.log
SG450:/var/log # ls -lha | grep afc.log
-rw-r--r-- 1 root log 970K May 5 15:49 afc.log
SG450:/var/log # ls -lha | grep afc.log
-rw-r--r-- 1 root log 991K May 5 15:49 afc.log
SG450:/var/log # ls -lha | grep afc.log
-rw-r--r-- 1 root log 1.1M May 5 15:49 afc.log
SG450:/var/log # ls -lha | grep afc.log
-rw-r--r-- 1 root log 1.1M May 5 15:49 afc.log
ATP mode is set to "Alert"
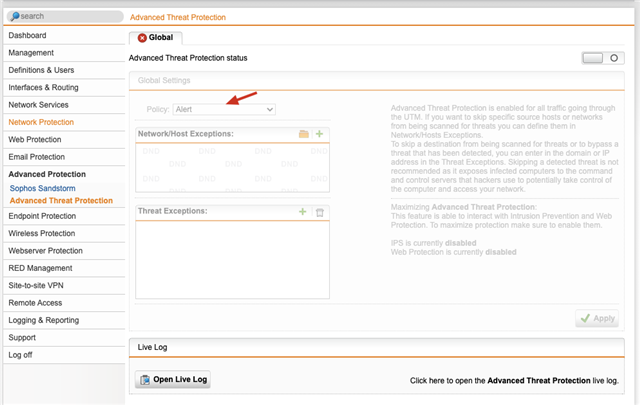
what are these messages?
how can we avoid the log from getting filled?
This thread was automatically locked due to age.