RE: UTM 9.314
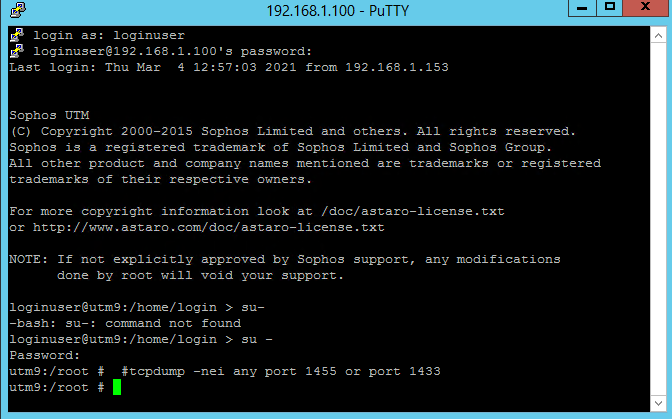
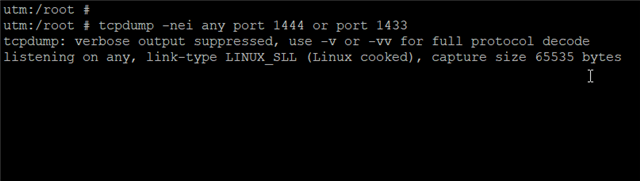
I created a DNAT rule to forward an alternate TCP port (14xx) to an internal SQL Server (at Default TCP Port 1433).
I use SQL Management studio to connect and it works for a while. A day or so later I try again, and it will not work.
The only way I can get it to work again is to restart the UTM 9 router.
I am not sure what I'm missing here but it's driving me crazy.
Not sure if I need another type of NAT to make this work all the time.
Any help would be appreciated.
This thread was automatically locked due to age.