Hi All,
After months (if not even years) of struggling with a poor performing wifi and numerous attempts to solve the problem (new ap, new cables new switches) I finally found out my problem to be the IPS turned on, on the lan side.
Before i got wifi speeds fluctuating between 9 to 25 Mbps, now with IPS set off i reach the actual 65 Mbps I am getting from my provider. My wired connection is also more stable (before it was also having with moments 35 Mbps and in other moments 55 or 60).
So I created this exception in IPS:
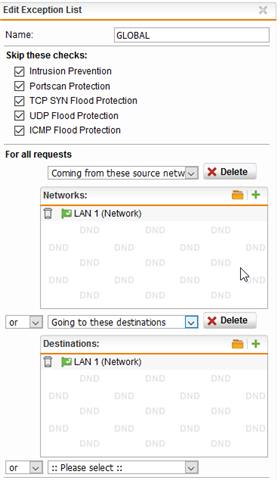
My questions:
1. Is it a dangerous setup and if yes by how far would you recommend not to you use it (eg: high or low risk, dangers involved..)?
2. Is it not maybe just enough that the WAN side is covered by IPS, why should I also do the LAN?
Keep in mind that for the first time in years I am very happy about the speed :) . To answer a possible suggestion upfront: no, making an exception only for the AP is not helping + the wired connection improved too. It is really the whole LAN segment.
Thank you in advance for your opinions / solutions!
Edward
This thread was automatically locked due to age.


