Hi,
I appear to be having an issue, where traffic relating to my Ring cameras is being blocked on my Sophos UTM Firewall. This blocked traffic is only occurring when I go to "Live View" one of the Ring cameras over the internal network, which causes the playback to quickly turn choppy and then disconnects. Using "Live View" on the cameras via an external connection, e.g. 4G does not cause this traffic to be logged.
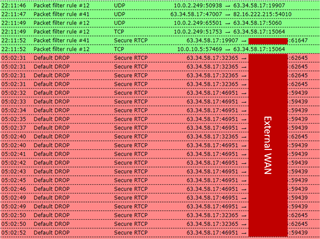
Looking at both the Live Log for the Firewall and looking back at the Firewall Log when running a search, I'm seeing a lot of blocked traffic for "Default DROP, Secure RTCP".
It seems like the initial connection is accepted, where shortly after the connection is rejected. I'm having real trouble troubleshooting this as whatever I change, appears to have no effect on the traffic being blocked. As a test, I created a ANY>ANY>ANY rule on the Firewall and moved the rule to the very top. Once done, I attempted live view on one of the cameras, but the Live Log for the Firewall was still showing "Secure RTCP" packets to be dropped.
In the attached screenshot of my Firewall Log, I noticed that at the start, "Secure RTCP" packets were being accepted by Packet filter rule #41. I tried to locate this rule on the Firewall, but I'm not sure how to determine the ID# of the Firewall Rules.
I do currently have a rule setup on the Firewall with the port numbers/ranges in which Ring have documented as being required for their cameras to function through a firewall. support.ring.com/.../205385394-What-Ports-Do-I-Need-to-Open-in-My-Firewall-for-Ring-Doorbells-and-Chimes-.
I appreciate any advice that you can provide :)
Cheers,
Richard
This thread was automatically locked due to age.