Hey everybody,
I'm trying to setup an IPSec Site to Site VPN tunnel from our local Sophos UTM running firmware 9.700-5 to their SecurePoint firewall.
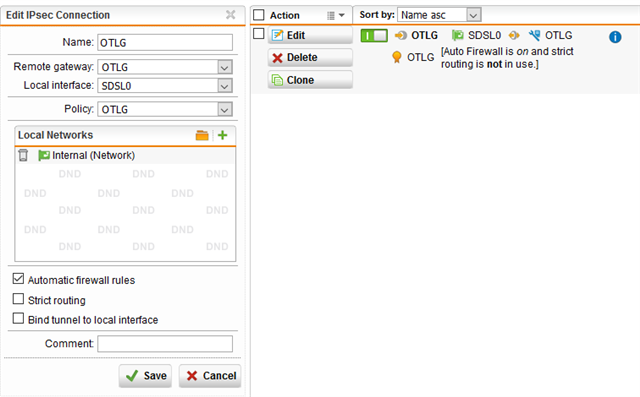
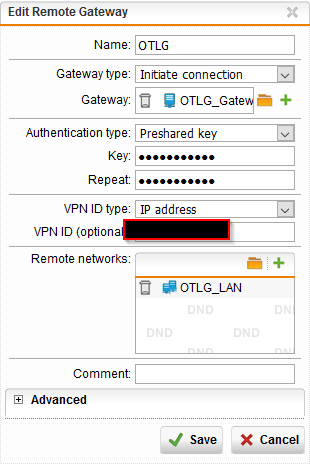
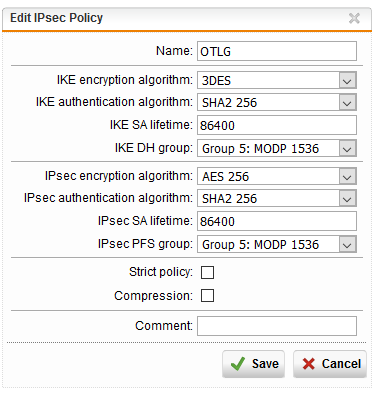
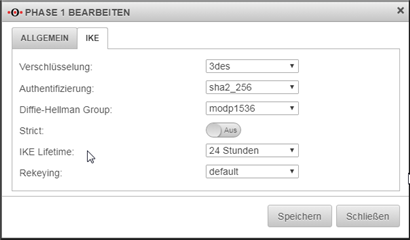
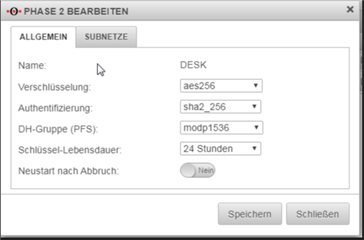
Here are some screenshots of the configuration on our end:
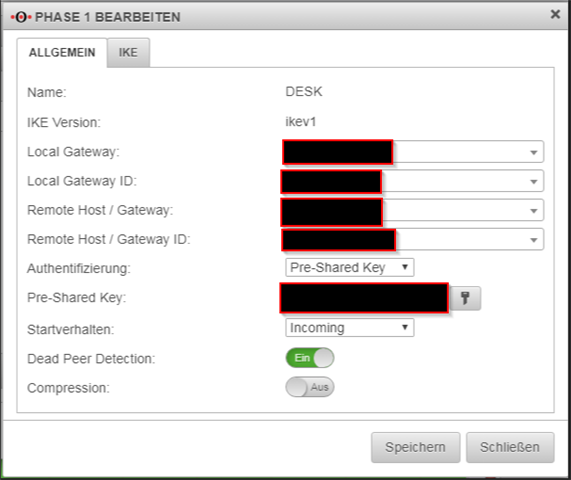
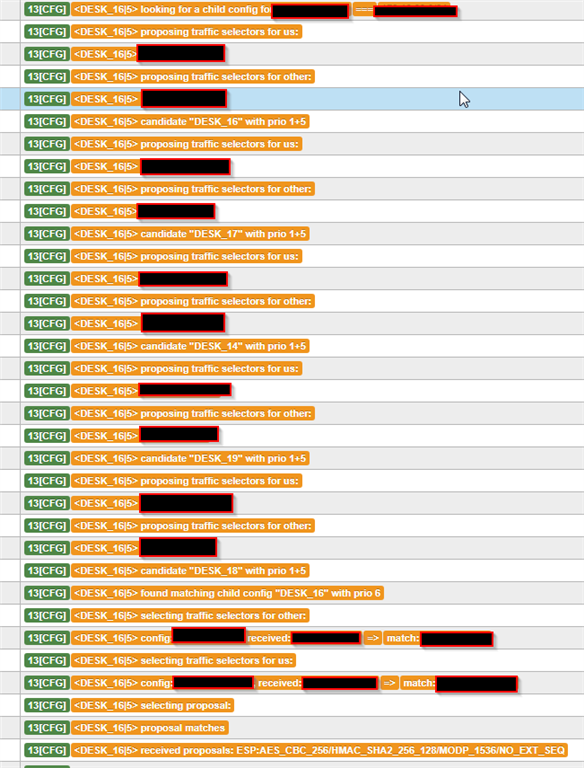
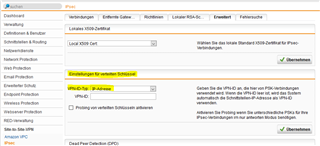
Here are some screenshots illustrating their end of the tunnel:
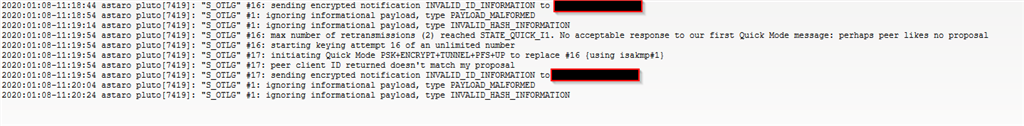
The log file on their end seems to suggest that the tunnel is coming up:
On our end however, I'm constantly receiving this error message:
This thread was automatically locked due to age.