We have been getting these email alerts to our network team from our main Sophos UTM since Tuesday morning.
=============================================================
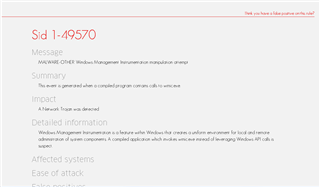
Message........: MALWARE-OTHER Windows Management Instrumentation manipulation attempt
Details........: https://www.snort.org/search?query=49570
Packet dropped.: yes
Classification.: A Network Trojan was Detected IP protocol....: 6 (TCP)
Source IP address: <SophosEndpointProtection-IP> Source port: 80 (http) Destination IP address: <Sophos-UTM-IP> Destination port: 64218
--
HA Status : HA MASTER (node id: 2)
System Uptime : 0 days 0 hours 18 minutes
System Load : 4.05
System Version : Sophos UTM 9.604-2
==========================================================
(2) The IPS log shows following summary
@12:18:34 action="drop" reason="MALWARE-OTHER Windows Management Instrumentation manipulation attempt" srcip="23.32.80.135" srcport="80" sid="49570" class="A Network Trojan was Detected"
@12:19:04 action="drop" reason="MALWARE-OTHER Windows Management Instrumentation manipulation attempt" srcip="23.76.197.134" srcport="80" sid="49570" class="A Network Trojan was Detected"
@12:19:35 action="drop" reason="MALWARE-OTHER Windows Management Instrumentation manipulation attempt" srcip="184.25.98.243" srcport="80" sid="49570" class="A Network Trojan was Detected"
(3) Since it is outbound on port 80, our 'WebProtection' shows this following sample summary...
12:19:04 method="GET" dstip="23.76.197.134" statuscode="200" cached="0" url="d1.sophosupd.com/.../1ab6fc7acbfce20ac8782ae88318a252x000.dat"
12:19:34 method="GET" dstip="23.32.80.135" statuscode="200" cached="0" url="http://d1.sophosupd.com/update/1ab6fc7acbfce20ac8782ae88318a252x000.dat"
12:20:04 method="GET" dstip="184.25.98.243" statuscode="200" cached="1" url="http://dci.sophosupd.com/update/3/25/325420ec2b9d8646efcfea111f80f01f.dat"
(4) The IPS log does not shows any detailed other that the SNORT# 49570 . Googling around found this link...
https://snort.org/rule_docs/1-49570
Any suggestions? We are getting 30-40 email alerts every hour.
Thanks,
Bob Gausman
This thread was automatically locked due to age.