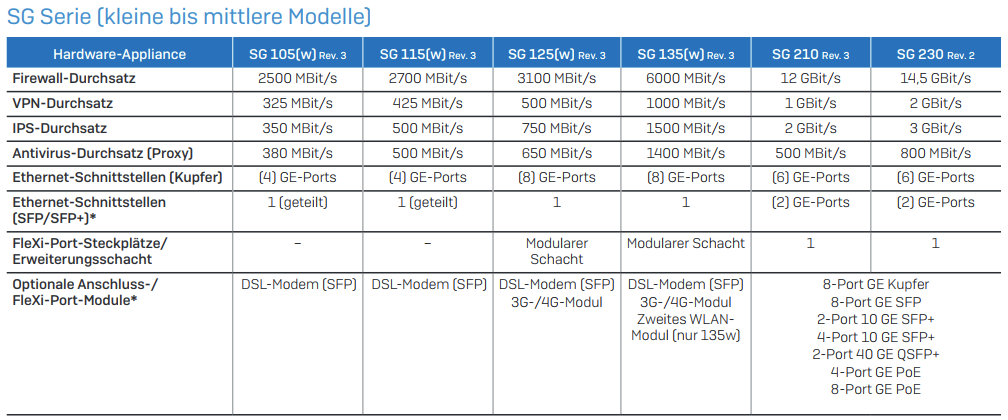
We're running a small SG115 unit at the office. It used to be quite sufficient for all our needs, however since a lot of things shifted to online work and the company has expanded we've had more and more trouble with performance.
The main culprit - Webserver Protection. This seems to be quite demanding when even a single client opens a lot of connections (example: a colleague working from home was restoring Nuget packages using our local DevOps Server feed as the source and this killed the SGs performance to such a degree that general internet connectivity was negatively affected).
I'm trying to find a way if I can't proxy our DevOps in some other way, but I'm also looking if upgrading the hardware is even a possibility. From what I can tell Sophos has a new line-up of network devices - the XGS series... which probably come preinstalled with the XG Firewall.
Now, to be honest, I'm not a fan of the XG Firewall. The entire control scheme seems a wee bit backwards AND it's still missing Let's Encrypt support, which I think kills it for us at this time. So... can the XSG series devices have UTM installed on them? Will Sophos be willing to convert / sell our current UTM license so that it works with a new XGS device should it be compatible?
This thread was automatically locked due to age.