Hallo Alle zusammen,
Ich habe einen IPSec Tunnel zu konfigurieren.
Aufbau
UTM <-> Fritzbox 7390 (static IP) <-> ASA (static IP) <-> interne Netze
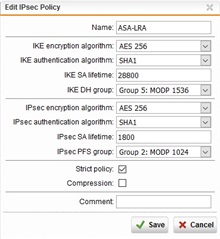
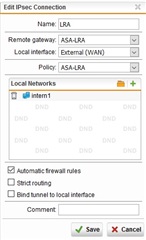
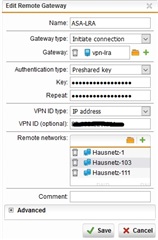
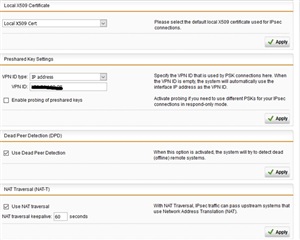
Ich habe die Konfig anhand der FAQ V7 Cisco gemacht und habe auch nach einigen Anlaufproblemen eine Verbindung aufbauen können.
Allerdings kann ich den Tunnel nur von der ASA-Seite her aufbauen. Wenn der Tunnel einmal aufgebaut ist, funktioniert alles hervorragend.
Hier noch ein paar Bilder
Und etwas Log-file
2016:08:23-09:00:21 asg12 ipsec_starter[20471]: Starting strongSwan 4.4.1git20100610 IPsec [starter]...
2016:08:23-09:00:21 asg12 pluto[20483]: Starting IKEv1 pluto daemon (strongSwan 4.4.1git20100610) THREADS VENDORID CISCO_QUIRKS
2016:08:23-09:00:21 asg12 pluto[20483]: loaded plugins: curl ldap aes des blowfish serpent twofish sha1 sha2 md5 random x509 pubkey pkcs1 pgp dnskey pem sqlite hmac gmp xauth attr attr-sql resolve
2016:08:23-09:00:21 asg12 pluto[20483]: including NAT-Traversal patch (Version 0.6c)
2016:08:23-09:00:21 asg12 pluto[20483]: Using Linux 2.6 IPsec interface code
2016:08:23-09:00:21 asg12 ipsec_starter[20477]: pluto (20483) started after 20 ms
2016:08:23-09:00:21 asg12 pluto[20483]: loading ca certificates from '/etc/ipsec.d/cacerts'
2016:08:23-09:00:21 asg12 pluto[20483]: loaded ca certificate from '/etc/ipsec.d/cacerts/VPN Signing CA.pem'
2016:08:23-09:00:21 asg12 pluto[20483]: loading aa certificates from '/etc/ipsec.d/aacerts'
2016:08:23-09:00:21 asg12 pluto[20483]: loading ocsp certificates from '/etc/ipsec.d/ocspcerts'
2016:08:23-09:00:21 asg12 pluto[20483]: Changing to directory '/etc/ipsec.d/crls'
2016:08:23-09:00:21 asg12 pluto[20483]: loading attribute certificates from '/etc/ipsec.d/acerts'
2016:08:23-09:00:21 asg12 pluto[20483]: adding interface wlan0/wlan0 172.16.28.1:500
2016:08:23-09:00:21 asg12 pluto[20483]: adding interface wlan0/wlan0 172.16.28.1:4500
2016:08:23-09:00:21 asg12 pluto[20483]: adding interface eth4/eth4 172.16.20.1:500
2016:08:23-09:00:21 asg12 pluto[20483]: adding interface eth4/eth4 172.16.20.1:4500
2016:08:23-09:00:21 asg12 pluto[20483]: adding interface eth1/eth1 192.168.10.66:500
2016:08:23-09:00:21 asg12 pluto[20483]: adding interface eth1/eth1 192.168.10.66:4500
2016:08:23-09:00:21 asg12 pluto[20483]: adding interface eth0/eth0 10.228.187.185:500
2016:08:23-09:00:21 asg12 pluto[20483]: adding interface eth0/eth0 10.228.187.185:4500
2016:08:23-09:00:21 asg12 pluto[20483]: adding interface lo/lo 127.0.0.1:500
2016:08:23-09:00:21 asg12 pluto[20483]: adding interface lo/lo 127.0.0.1:4500
2016:08:23-09:00:21 asg12 pluto[20483]: adding interface lo/lo ::1:500
2016:08:23-09:00:21 asg12 pluto[20483]: loading secrets from "/etc/ipsec.secrets"
2016:08:23-09:00:21 asg12 pluto[20483]: loaded PSK secret for x.x.x.x(fritz) x.x.x.x ASA
2016:08:23-09:00:21 asg12 pluto[20483]: listening for IKE messages
2016:08:23-09:00:21 asg12 pluto[20483]: added connection description "S_LRA"
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: initiating Main Mode
2016:08:23-09:00:21 asg12 pluto[20483]: added connection description "S_LRA"
2016:08:23-09:00:21 asg12 pluto[20483]: added connection description "S_LRA"
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: received Vendor ID payload [RFC 3947]
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: ignoring Vendor ID payload [FRAGMENTATION c0000000]
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: enabling possible NAT-traversal with method 3
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: ignoring Vendor ID payload [Cisco-Unity]
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: received Vendor ID payload [XAUTH]
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: ignoring Vendor ID payload [ec3755d03316d64a0ee3fa31a870370f]
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: ignoring Vendor ID payload [Cisco VPN 3000 Series]
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: NAT-Traversal: Result using RFC 3947: i am NATed
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: received Vendor ID payload [Dead Peer Detection]
2016:08:23-09:00:21 asg12 pluto[20483]: | protocol/port in Phase 1 ID Payload is 17/0. accepted with port_floating NAT-T
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: Peer ID is ID_IPV4_ADDR: 'x.x.x.x ASA'
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: Dead Peer Detection (RFC 3706) enabled
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: ISAKMP SA established
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #2: initiating Quick Mode PSK+ENCRYPT+TUNNEL+PFS+UP {using isakmp#1}
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #3: initiating Quick Mode PSK+ENCRYPT+TUNNEL+PFS+UP {using isakmp#1}
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #4: initiating Quick Mode PSK+ENCRYPT+TUNNEL+PFS+UP {using isakmp#1}
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: ignoring informational payload, type NO_PROPOSAL_CHOSEN
2016:08:23-09:00:21 asg12 pluto[20483]: "S_LRA" #1: received Delete SA payload: deleting ISAKMP State #1
This thread was automatically locked due to age.