I have a server running UTM in Hyper V with 3 Interfaces.
Interface 1: Goes to a modem for internet connection
Interface 2: Goes to a Cisco Meraki 220 switch
Interface 3: Virtual switch for other virtual machines running on the server
I split the subnets between interface 2 and interface 3 making the physical switch 192.168.1.X and Interface 3 the Virtual switch 192.168.2.X. Using Sophos to handle DHCP on each interface.
I now have a Server on the Physical Network (Int 2) that I want to get a DHCP address from Virtual Network (Int 3).
I want to have two subnets one for personal devices 192.168.1.x and one for a homelab 192.168.2.x. I think the proper way to do this is by setting up two VLANs: VLAN 10 (192.168.1.x) and VLAN 20 (192.168.2.x). I believe I can assign ports on the meraki switch and route them in the sophos to do this.
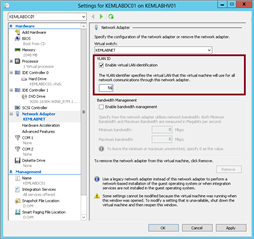
I tried to set the port on the Meraki switch to an access port tagged VLAN 20, and set up a VLAN Interface on the Sophos Router to route the traffic to the virtual network. Although I still cant get it to see the 192.168.2.X DHCP server.
I think what I want to do is assign IPs based on VLAN tag not interface. It shouldn't matter if a device is on the virtual switch or the physical. I can tag the port with a VLAN and Sophos will then assign the correct IP from the subnet for that VLAN.
This thread was automatically locked due to age.