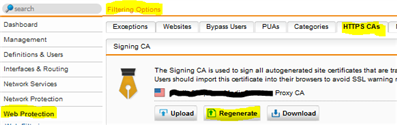
Hello,
got message from UTM:
1 certificate(s) will expire within the next 30 days:
Proxy CA
when I clicked Regenerate button, next day - no SSL VPN client could connect, so I restored backup...
but I do have problem: some users have certificate for Proxy CA expiring on 25.11.2017.
I have "permanent": expiring 01.01.2038.
after backup restore, all clients can connect with SSL VPN client...
but I can't connect on User Management page for users from my LAN to DLoad latest VPN package, all VPN users have Remote Access enabled..
checked link bellow, but as I said - regenerate isn't solving issue at hand...
https://community.sophos.com/kb/en-us/126962
Thanks for any suggestion.
KJuric
This thread was automatically locked due to age.