Hello guys,
I´m trying to setup wifi with RADIUS authentication so my user can login into Wifi with their AD credentials.
I´ve installed NPS on my Win 2008 server added it to UTM as a RADIUS server but unfortunately users can not log in from mobile devices
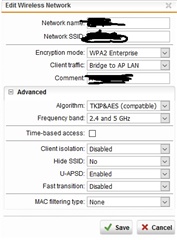
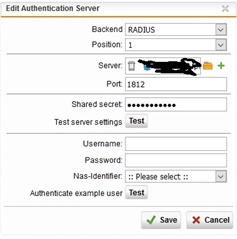
Here is my setup in UTM
Wifi
Radius
Thanks for any help!!
Jiri
This thread was automatically locked due to age.